This module focuses on monitoring and maintaining high network performance. There may be various reasons due to which the network performance is affected. For this there are network appliances which boost up the performance of the network. These appliances include load balancer, proxy server, content filters and VPN concentrators. In this module we will discuss all of them.
Apart from so many software tools that are available to troubleshoot network related problems, there are some hardware tools also. We are going to discuss some of them including cable tester, toner probe, cable certifier, butt set, crimper, punch down tool, protocol analyser, loop back plug, TDR, OTDR, multimeter and environmental monitor. These tools are a network administrator’s friend which he should always keep in his set. We will also discuss some software tools to troubleshoot network related issues like protocol analysers, throughput testers and connectivity software.
Networking commands can help us understand the working of the network. They give a clear insight of what is going on right and where is the problem. There are various commands which give a lot of information about the network and its functionality. The more the information is available the more the administrator is able to understand the working. Also some logs are made on the system automatically which store different kind of information regarding the nature of traffic. A well-documented network is easy to manage and upgrade. Here we will also discuss different documentation techniques. They are very essential for future reference in case there is any change in the administration.
Module 4.1
In this section we will discuss network appliances which provide additional network functionality. They are specialised electronic devices which enhances the capability of existing hardware and software. In order to cut cost and ease remote management network appliances are a useful medium. Here are a few –
- Load Balancer – The load balancer is the network appliance that is used to distribute the workload across devices. Load balancers transparently distribute using algorithms. Load balancers are also capable of DOS protection and caching. With the use of load balancers, the capacity and reliability of applications can be increased as burden on servers which are busy in managing high level tasks is reduced.
Load balancers avoid overloading of any single device and can be implemented with hardware, software, or a combination of both. Hardware based solutions have specialised processors with proprietary software already installed on the machine. Software solutions are cheaper and flexible as they run on commodity hardware. There are certain industry standard algorithms used for load balancing like
- Round Robin – Sequential distribution of requests across the group of servers.
- Least Connections – The server which has least current connections to the clients is sent a new request
- IP Hash – The decision of which server receives the request is done on the basis of the IP address of the client.
- Proxy Server – A proxy server is a network appliance that is able to work in between our computers and the Internet. Proxy servers offer additional privacy and content filtering as well as increased performance and caching. Caching will improve user response time as if more than one request comes at the same time they can be kept in the proxy cache. Proxy server can also be used to filter request and prevent certain users from accessing specific information. It can also be one of the components of a firewall.
- Content Filter – A content filter is a network appliance that is able block traffic based on rules and filters. Traffic needs to flow through a device and it can be evaluated in different ways such as keywords in the URL or the category of web sites. Content filters can be used in many different environments such as parental controls and office productivity to prevent employees from spending too much time on certain web sites. Content filters can be hardware, software or cloud-based.
Content filtering is implemented by matching string of characters. If the requested content matches the filtered string, it is now allowed. It is usually implemented as a part of firewall. Different types of content can be filtered including emails, games, instant messengers, VoIP, P2P, files, protocols, websites, etc.
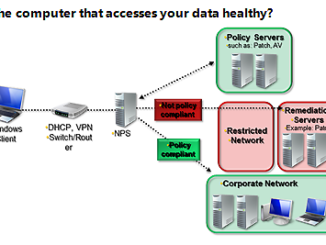
- VPN Concentrator – A VPN concentrator is a network appliance that provides a connection point for remote users. The end users initiate the VPN client and connect to the public Internet. The data flows through the encrypted tunnel to the concentrator and then the concentrator authenticates. The VPN concentrator provides encryption and prevents RAS exposure and is capable of standing alone or implementing into the edge router.
It is a type of router device which creates and manages VPN communication infrastructures. Tasks performed by VPN concentrators include Establish and configure tunnels user authentication, assignment of tunnel/IP addresses to users, encryption and decryption of data and ensuring end-to-end delivery of data. They usually find their application at places where the requirement is for a single device to handle a very large number of VPN tunnels.