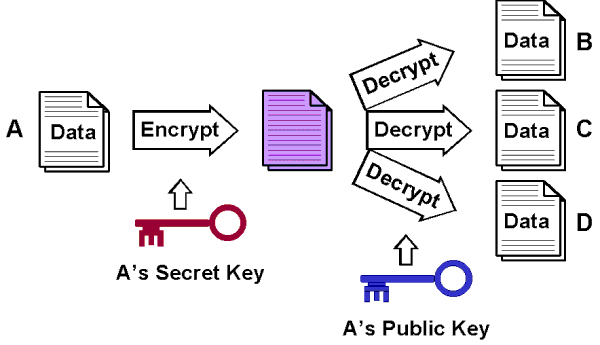
A Public Key Infrastructure deals into the distribution and identification of the public encryption keys. This enables users and computers to securely exchange data over networks such as internet and verify the parties.
It is possible to encrypt and exchange the information,ensuring confidentiality without the Public Key Infrastructure (PKI), but there would be no assurance of the identity of the other party. If the information is transmitted over the internet, it completely relies on the PKI for the security.
What are the elements of PKI?
The PKI generally consists of hardware, software policies and standards that would manage the creation, administration, distribution and revocation of keys.
A PKI may include a trusted party called a certificate authority CA, that provides the root of trust and provides service to authenticate identity of individuals. A registration authority would issue certificates for specific uses permitted by the roots.Certificate database that contains the certificate requests, issues or revokes the certificate. The certificate store that issues certificates and keys.
All security controls need encryption of data that comes down to authentication and access control. Although Encryption is a powerful tool, but it will be useless unless the data can be decrypted. Now, determining who has the right to decrypt the data becomes another point of contention. The organization may deploy appropriate set of checks to preventing the malicious users to hack the system and the important information.
