
CSSLP Tutorial: The third element of module 1 involves system architecture.
When we are talking about the architecture of a system, we are talking about design and about the internal structure upon which other systems will be built. The main priority of designing system architecture, is to meet the goals and requirements of the business. The whole point of what security is made for is to support the business side of things.
CSSLP Tutorial: Graphics or pictures can help with understanding.
There is a graphic of a ladder shaped icon and the element being supported by all the other levels is the business architecture. Then, the business architecture drives the information architecture which then Prescribes and Identifies Data architecture. The data architecture is supported by the delivery system architecture, the hardware, the software and communications. Then the standards and/ or requirements is a driving force at each level while simultaneously, the feedback from the data architecture being provided all the way up the ladder to the business architectures. Security is figured in because it brings benefit to us by supporting business as well. So, when we look at the question of how much security is enough, “Just enough” is an answer which can be depicted in the following diagram.

This is where security’s needs and business objectives must be kept in balance with one another. We want to provide sufficient risk management without compromising our business objectives. So, the system architecture must be built with keeping this balance in mind. Rather than added on later as a band-aid or “duct-taped” added on later, security must be more integrated into the design to be a functional design.
CSSLP Tutorial: When we talk about the architecture of a system,
There are some things we need to look at such as elements which make up the trusted computer base (or TCB). It is the total of all hardware, software, and firmware that enforces the security policy of a system. The TCB is a term that’s been around for a really long time, but maybe hasn’t been really in use for the last 20 years, perhaps since 1999. It was first discussed in the “Orange Book” . This was the publication published by the Department of Defense (DOD)and part of the Rainbow Series, which reported security requirements for networks, databases, audit systems, password guidance and so on which lead to protection of government classified information. They originally published the Trusted Computer System Evaluation Criteria as what we now refer to as the TCB.
There’s some really good ideas, important ones we can use today, from this series of older computation books. There’s a couple of elements that really pop out. One is the security parameter, and another is the reference monitor. The third is the security kernel.
CSSLP Tutorial: It doesn’t matter how many mechanisms you put into your OS,
But if your BIOS can be compromised, then none of that matters. What’s really important is the memory, the CPU, all of those elements must be where we can trust them for security and performance.These must support the security policy of the system and should not be able to violate the security policy. All of these together are referred to as the Trusted Computer Base.
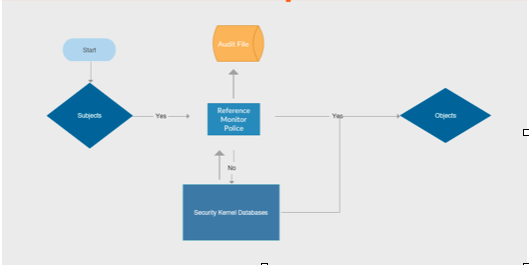
CSSLP Tutorial: A couple of the elements that are of the TCB are the Security Parameter, the Reference Monitor and the Security Kernel.
If we could put all these elements into one circle, then that one enforcing border would be referred to as the security perimeter. The reference monitor is metaphorically like the laws of the land. The security kernel is like the police, holding to the same metaphor. The laws are like the rules where for example, the lists of do’s and don’t of your system. There may be access control lists in the reference monitor. When a subject accesses an object like in the above flowchart, then the reference monitor has to be verified. This is like the three attempts at the password as an example. Then, the enforcement of the reference monitor is being carried out by the security kernel. In the metaphor, laws are not any good if there isn’t some way to be able to enforce their enactment. So, in the three attempts at a password example, the security kernel would be the actual software to log the person out or block the account from that subject on the third failed attempt.


So, again, it’s important to be able to trust your computer and the central processing unit as you are building your system architecture. First, the security system (ISS) is integrated with the structural programming. How that’s done is with Trusted Computer Base (TCB) elements which include the border surrounding your structure, the laws of the land and the police which enforce those laws and keep the subject from accessing the object if they can’t follow the rules of your built-in security system, and therefore, shouldn’t have that access..
