What is a Buffer Overflow?
A buffer overflow, or buffer overrun, is an anomaly where a program, while writing data to a buffer, overruns the buffer’s boundary and overwrites adjacent memory locations.
In programming terms it can be said that when we allow user input or service input externally, we write a data to a variable and that variable is generally saved in computer’s random access memory. If the user enters more characters then specified like we have allocated 500 characters and user enters 600, then 100 characters will buffer overflow into adjacent memory locations. These adjacent memory locations are actually executable memory locations. From there one can actually execute code and make the application vulnerable.
Buffer Overflow Walkthrough
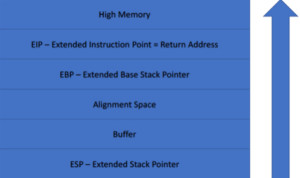
Figure1. Buffer Overflow Walkthrough
The buffer fills from the bottom up. The working of buffer may be different for different architectures but the concept is same. As we start filling the characters in the buffer for e.g. for a first name of 500 characters, filling will start downwards. The stack is actually the metadata of where the data is. So the data will start filling from the stack then the 500 words will go in the buffer. If there are more characters they will go into the alignment space. Then it will hit the EBP and finally reach EIP. EIP contains the next instruction for the application. If the 100th character goes in the EIP where the application is supposed to execute, at the 600th character one can actually get the application to execute code which is not supposed to do and is an anomaly. Data execution should not be done through memory, it should be done by CPU.
What are the countermeasures?
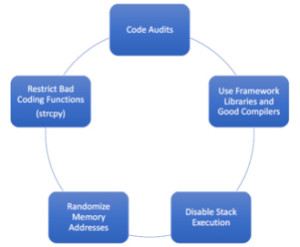
Figure2. Buffer Overflow Countermeasures
Code Audits – Writing programs that actually do not have buffer overflow exploiting them. This can be done by code audits and making sure that the code is reviewed before being submitted.
Use Framework Libraries and Good Compilers – There are libraries and compliers which make sure that there are no buffer overflow vulnerabilities. A good compiler with a good framework library is a good option.
Disable Stack Execution – In Windows terms, this is called DEP or data execution prevention. We must make sure that the OS doesn’t allow execution of data in the stack.
Randomise Memory Addresses – If the buffer is sequential, it is easier to craft a buffer overflow, but if we randomize the memory and the OS writes the characters to totally different random places all over the memory then buffer overflow becomes very difficult.
Restrict Bad Coding Functions (strcpy) – Bad coding functions for e.g. a string copy function ‘strcpy’ should not be used.
Ethical Hacking Tutorial: Buffer Overflow Theory Video:
