What is Denial of Service?
 Figure 1. Denial of Service
Figure 1. Denial of Service
Denial of Service (DoS) is the interruption in an authorized user’s access to a computer network, typically one caused with malicious intent. Distributed Denial of Service (DDoS) attack occurs when multiple systems flood the bandwidth or resources of a targeted system. In distributed DoS there are more than one systems which are included in the attack while in denial of service there is one system involved.
What are the goals of Denial of Service?
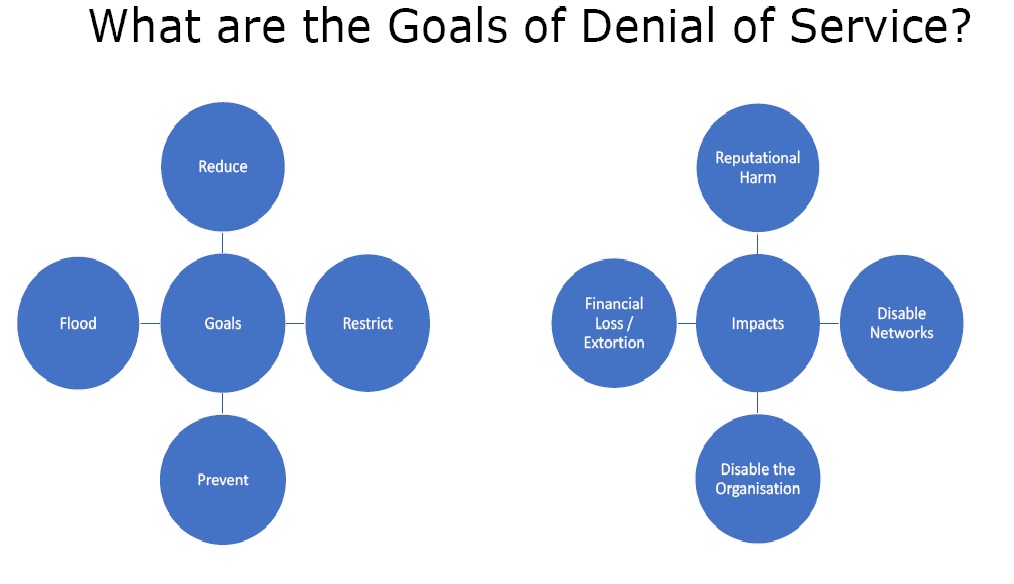 Figure 2. Goals
Figure 2. Goals
- Reduce – It is reducing the availability of service.
- Restrict – In this people are restricted from accessing a certain service by denial of service attack.
- Prevent – It is preventing the normal use of a service or system e.g. if one takes a website offline, then no one can use it.
- Flood – In this the system resources are overwhelmed and they are not able to respond normally.
The impacts of DoS can be very severe. Here are these –
- Reputational Harm – The reputation of the target may be harmed in the market.
- Disable Networks – Nobody can use the network after the attack.
- Disable the Organisation – The attacker can use the information about the organisation and disable it completely e.g. by using account lockout.
- Financial Loss / Extortion – There can be massive loss to the organisation.
What are Denial of Service techniques?
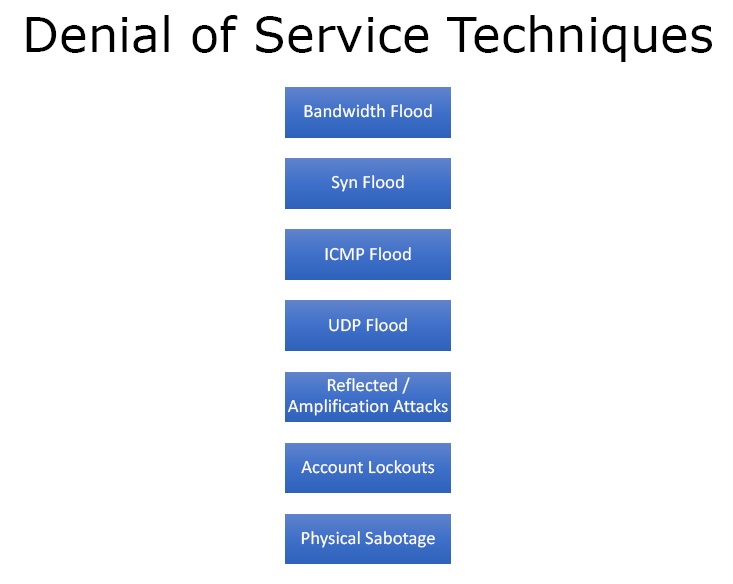 Figure 3. DoS Techniques
Figure 3. DoS Techniques
- Bandwidth Flood – In this the attacker can send packets such as to soak up all the bandwidth so that any other person trying to access the system would not be able to do so.
- Syn Flood – It takes advantage of the TCP/IP handshake and opens up a syn connection but doesn’t complete the connection. So the web server is waiting for the connection to complete and by opening up thousands of such connections it takes up the server’s resources.
- ICMP Flood – By crafting special packets in the ICMP ping request one can set the size of each packet. Then thousands of systems send packets simultaneously causing denial of service attack.
- UDP Flood – In this UDP packets are used.
- Reflected / Amplification Attacks – In this a whole bunch of different computers spoof the IP address of the victim and then request DNS or NTP traffic. The response then goes to the victim instead of the attacker as the IP address was spoofed.
- Account Lockouts – In this one writes script and lockout accounts for an entire organisation.
- Physical Sabotage
What are the countermeasures?
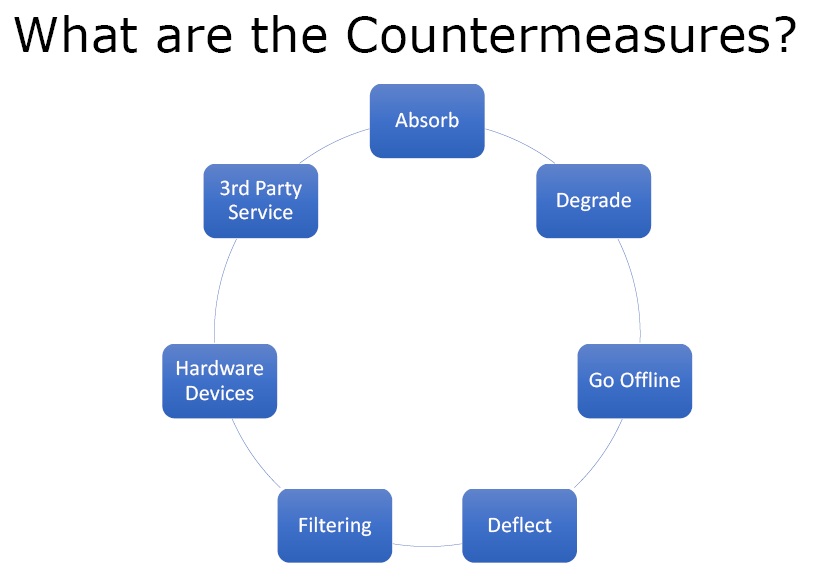 Figure 4. Countermeasures
Figure 4. Countermeasures
- Absorb – Absorb the attack by increasing the resources.
- Degrade – Compromise with the degraded service.
- Go offline – Go offline and intimate the audience that they cannot render the services due to attack.
- Deflect – With the help of network engineers the victim can deflect the IP of the attacker to a black hole somewhere so they don’t actually end up hitting the server that is under attack.
- Filtering – Block the attacking IPs entirely and does not accept any connections from them.
- Hardware Devices – There are hardware devices that perform deflecting and filtering automatically.
- 3rd Party Service – There are third part services that offer DoS protection.
Ethical Hacking Tutorial – Denial of Service Theory Video: