What are Mobile Platforms?
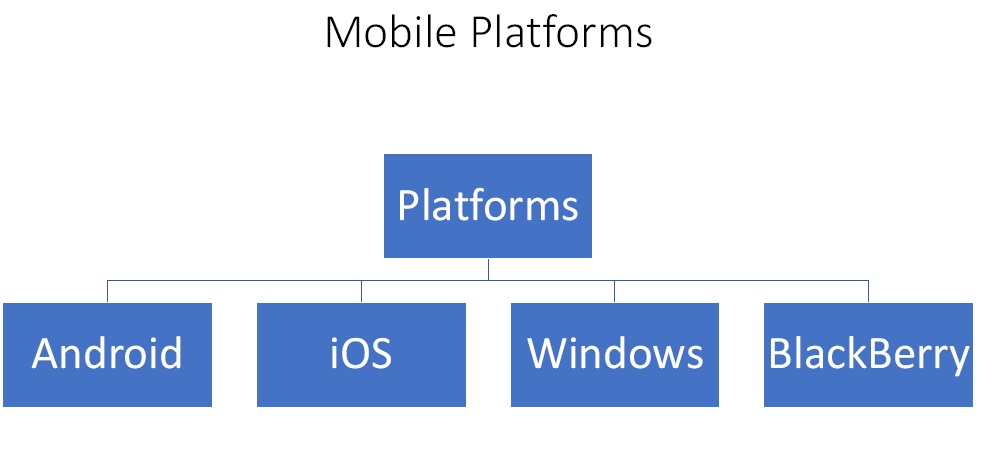
Figure1. Mobile Platforms
- Android – It is the biggest and by far most popular. So it is also the biggest target.
- iOS – The next biggest platform is Apple’s iOS. It seems to be more secure than Android.
- Windows – Windows Mobile which is now known as Windows 10. Its market share is reducing day by day.
- BlackBerry – It is not used much nowadays.
What are Mobile Vulnerabilities?
- Operating System – The first vulnerability is actually found in the Operating System. There are specific vulnerabilities in each OS that bad actors exploit to gain access or implant malware, etc.
- Apps / App Stores – There are a few rogue app stores that hackers have put out into the market from people download malicious apps.
- Malware – There are malwares that are specifically written for mobile platforms and perform activities like blocking device, data stealing, send SMS or spoof email, etc.
- “Jail Breaking” – It is also known as routing. In the attacker try to get access to the actual OS.
- Privacy – Mobile device is a personal property and if it gets compromised in any form it is a big privacy mobile vulnerability.
- Physical Theft – Because of the size and portability property of a mobile device, it can be easily stolen and the whole device is automatically compromised.
What are Mobile Attacks?
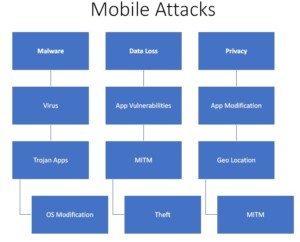
Figure2. Mobile Attacks
- Malware
- Virus
- Trojan Apps
- OS Modification
- Data Loss
- App Vulnerabilities – They can leak data and privacy.
- MITM – Man in the middle attack is a very real threat for mobile devices. One can sniff passwords, credential, steal cookies, etc. and all the attacks that are there for web application hold true for mobiles also.
- Theft
- Privacy
- App Modification
- Geo Location
- MITM
What are the countermeasures?
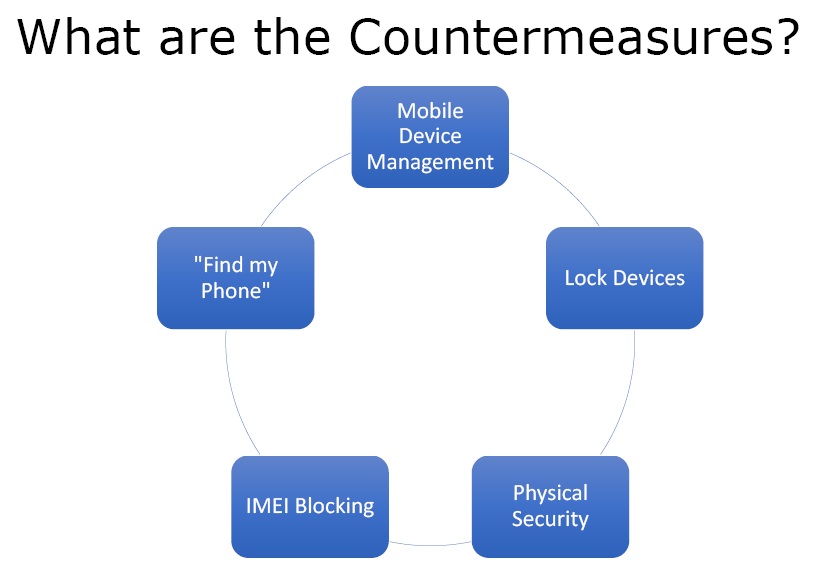
Figure3. Countermeasures
- Mobile Device Management – It includes enterprise-grade software services and hardware that control mobile device access to the organisation’s data and services.
- Lock Devices – One must always set a lock whether it is a PIN code, lock pattern, or any other. a device with an authentication is always better than a totally open device.
- IMEI Blocking – If the device gets lost or stolen, one can ask the ISP for IMEI blocking.
- Physical Security – Mobile devices are always with the person and the most important countermeasure to protect a mobile device is its physical security. The device has got the entire digital identity of the person and can prove to be very unsafe if lost or stolen.
- “Find my Phone” – In Android, Apple and Microsoft ecosystems, there is a popular app called “Find my phone”. one can register the device on it which then talk to a back-end service and give real time information about the device. But there is a disadvantage to it also as the back-end carrier will always know where one is.
Ethical Hacking Tutorial – Mobile Attacks Theory Video: