Web Credential Harvester
We can use social engineering tools on Kali Linux to create web credential harvester. They help us to create fake websites or emails which trick people to give their credentials or click on a link, etc.
Open the social engineering toolkit.
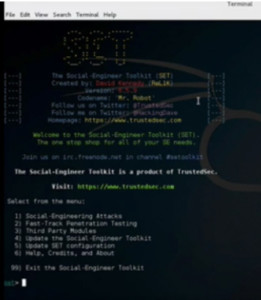
Figure 1. Social Engineering Toolkit
SET has got a lot of ways to create social engineering attacks. But one thing to be kept in mind is that many of these exploits are already vulnerable or have been found by various companies like Microsoft, etc. so many of them will only work on untouched machines.
Here we will select option 1, for social engineering attacks and then we select option 2 for website attack vectors. As we are going to perform a credential harvester attack, hence we will put up a fake site, have people into their credentials and capture those credentials so that we can use them later.
Select option 3 and then choose a web template that is already created. We can also clone a site or do a custom import.
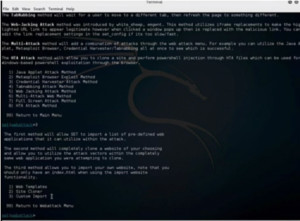
Figure 2. SET Options
Creating a fake Website
Select option 1 for website template. Now we will put the IP address of the actual server that is hosting this social engineering fake website. Here we are doing it on one machine but you may want to put this on a server that is exposed to the internet. Here we will use the loopback adapter so we will enter ‘127.0.0.1’. We will choose the Google template.
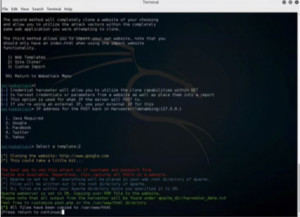
Figure 3. Create fake Website
Now we can see that it has given us the apache and all files are copied to /var/www/html. On another window we go to this location in the file system. If we do ls we can see that it has a .txt file, index.html and post.php.
Go to the browser and enter http://127.0.0.1. It will open the Google sign in page.
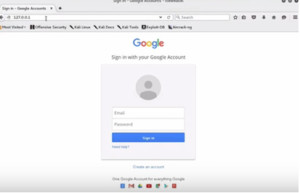
Figure 4. Fake Google Login Page
The only way one can know that it’s a replica is by looking at its name in the address bar. But if this is sent as a link in the email or message and open it then chances of doubt reduces. Now we will put the email address and password and then click sign in. It takes the user back to Google home page. It worked nicely but didn’t sign in. As a user we would try to sign in again. But here lets see what has happened in the background.
We will go to the location where the harvester files were saved. Open the .txt file. We can see that it has actually captured those credentials very clearly. It has the exact email address and password entered on the fake Google sign in page.
So with a very simple quick setup on social engineering toolkit setting up a fake Google sign in page we have managed to trick someone into giving their username and password. We can use this method for any number of different credential harvesting like Yahoo, Twitter or any custom one.
Ethical Hacking Tutorial: Social Engineering Lab Session Video:
