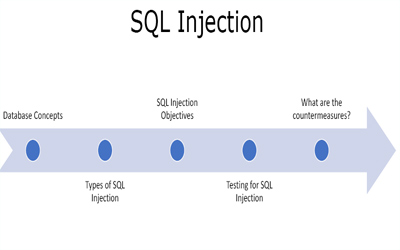
Database Concepts
A database is a collection of data. Companies, enterprises, websites and many other store their data and other useful information in the database. It may be the information which is not allowed for everyone to view or modify. The database is kept on a database server. There may be one or more databases on the server. Each database has one or more tables, each table has multiple columns and then columns have rows where the data actually resides.
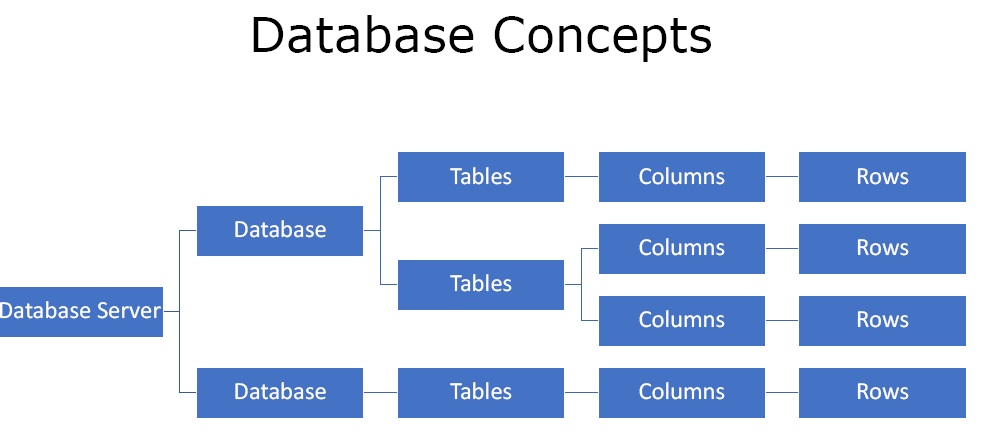
Figure 1. Database Concepts
What are the Types of SQL Injection?
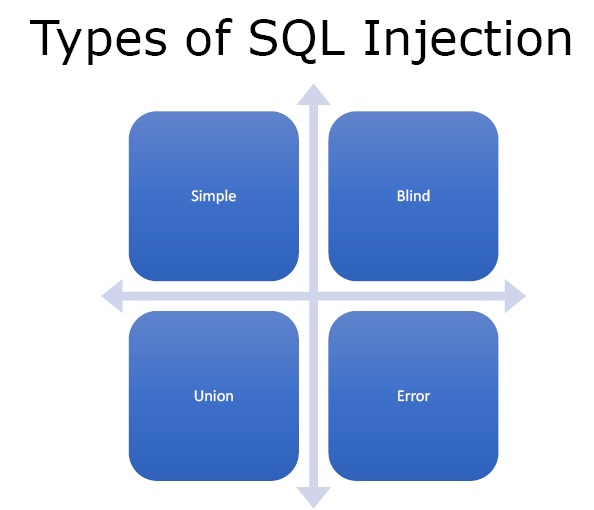
Figure2. Types of SQL Injection
- Simple – In this one just puts an invalidated SQL script and gets something in return.
- Blind – In this after writing the script the data is not returned in the browser but the script or data is still being injected into the database.
- Union – In this we join two different sets of data together and see what error messages or what data disclosure we can get.
- Error Based – It is generally used for disclosure. If we keep throwing errors into the SQL database and getting error messages back eventually the database starts to build itself.
What are SQL Injection Objectives?
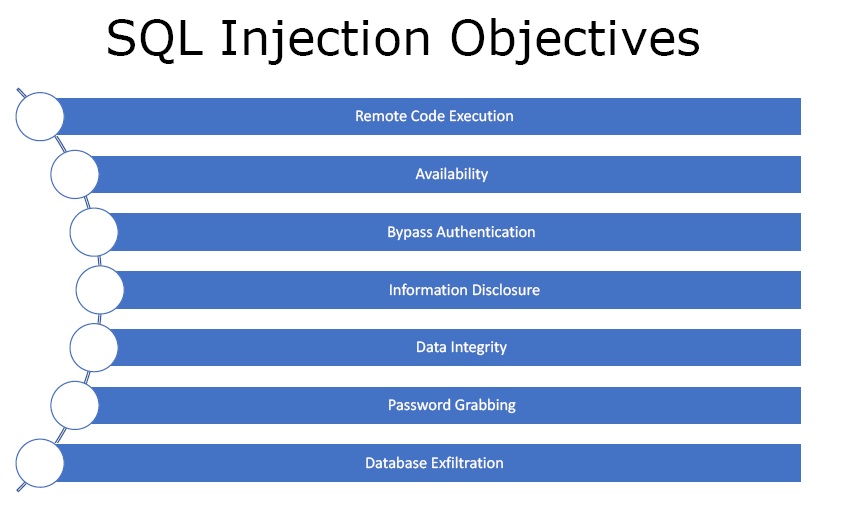
Figure3. SQL Injection Objectives
- Remote Code Execution – One can inject scripts or code into a database and run them on the server.
- Availability – One can take the server offline or drop the database if the databases are under SQL injection.
- Bypass Authentication – SQL injection can be used to bypass the need of passwords and get access to the system without the need of password.
- Information Disclosure – One can view or even distribute the whole database or use it maliciously.
- Data Integrity – One can change the data in the database or change the values.
- Password Grabbing – One can get all the passwords through SQL injection.
- Database Exfiltration – One can get into the entire database.
How to test for SQL Injection?
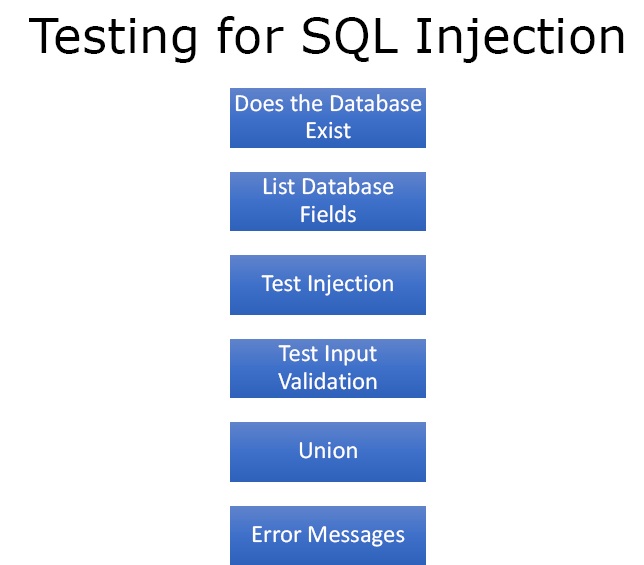
Figure4. Testing for SQL Injection
- Does the Database Exist – There must be a database to perform SQL injection.
- List Database Fields – We can enumerate the database name, tables and columns.
- Test Injection – Check whether we can change the integrity of the data.
- Test Input Validation – Check whether we can write scripts into the database and what type of data like text, images, numbers, etc. it will accept.
- Union – Can we put unions between tables and try to get the database act erratically so we can get more information.
- Error Messages – Error messages can give a lot of information about the database.
What are the Countermeasures?
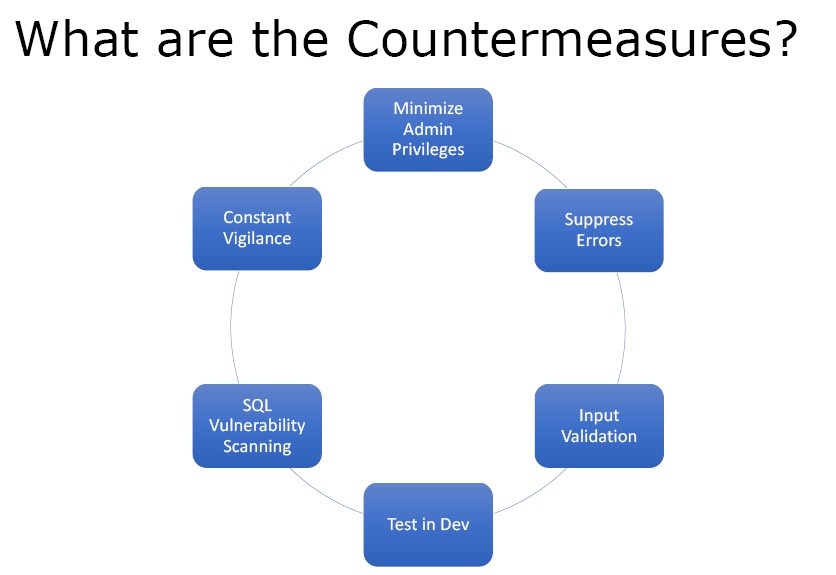
Figure5. Countermeasures SQL Injection
- Minimize Admin Privileges – The user interacting with the database on behalf of the web application should have minimum privileges.
- Suppress Errors – Error should be either very short or no errors so that the information is not disclosed. Debug mode should be set to off.
- Input Validation – One must make sure that anything that is coming untrusted from outside must be validated.
- Test in Development – Penetration testing along with other forms of testing should be done to make sure that the application is secure.
- SQL Vulnerability Scanning – One should run vulnerability scans against the database or web application before attackers do that.
- Constant Vigilance – One should always keep an eye on the database and monitor it for changes, logs and views the error messages that are being generated so that any SQL injection attack can be stopped on time.
Ethical Hacking Tutorial: SQL Injection Theory Video: