In system hacking we will discuss the following tools –
Hydra – It is a password dictionary attack tool.
Armitage – It is the front end for the metasploit framework for exploiting vulnerabilities in service.
In this along with the Kali Linux machine, we will also use a virtual machine which runs the metasploitable framework. This can be downloaded from the internet. It is very helpful for testing exploits and labs, etc.
First of all we will perform a nmap scan on the IP 192.168.1.108 and see which ports are open. –sT is to perform a full scan.
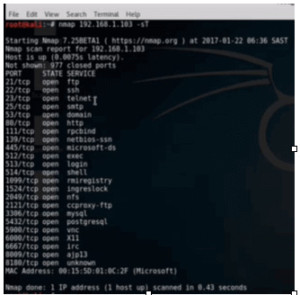
Figure1. nmap scan
We can see that ftp, ssh and telnet are open, so we can remote into this server. Now we will have to get the username and password. Here we have got a username ‘msfadmin’ which we will use for this session. To do the password attack we will first use Hydra.
If we simply type hydra at the command prompt, we will get the whole list of options.
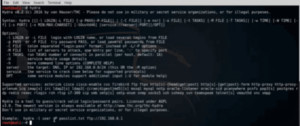
Figure2. Hydra options
The last line gives an example of the usage of the command. Here the passlist.txt is the list of password or dictionary list that we can either create or download from the internet. For this demo we have created a password list subs.txt with the real password also in it i.e. msfadmin. So the command would be –
Hydra –l msfadmin –P subs.txt ssh://192.168.1.103
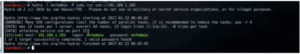
Figure3. Hydra output for ssh
As we can see, it has given the password in green. It can also be used to attack other ports. We can do this for ftp also.
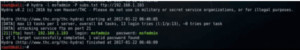
Figure4. hydra output for ftp
Now we will look at Armitage. It is specified as a menu item in Kali Linux. In order to launch armitage, one must block post gres SQL service and the command for that is ‘postgressql’. We have Armitage up and running.
Figure5. Armitage
First of all we will add a host to the attack workspace. Go to the hosts menu, and click Addhosts. An input box will come, enter the portable server i.e. 192.168.1.103 and add. It will be shown on the host. Now right click on the host and select scan. It will run nmap and other scans in the background and find all open ports. After the scan is complete we will get available options.
Now go to the attacks menu and select ‘Find Attacks’. Now it will query all the open ports and compare them to the exploit database which it already has on the Kali Linux system. After it has finished, we will right click on the host and see that an ‘Attack’ menu is added. There are a whole host of attacks. We will attack the samba service specifically the ‘usermap_script’. On clicking that a message box will appear and we will launch attack with default settings. The icon of the host changes to red indicating that the attack is successful.
When we right click on the host, we will find one more menu item ‘Shell’ is added. With this we can interact with the server like adding user and other vulnerabilities or upload files, etc.
Ethical Hacking Tutorial: System Hacking Lab Session Video:
