What is this module about?
This module is an overview of the last three phases. This is an introductory module to the rest of gaining access, maintaining access and covering tracks module that we will study after this. The purpose of this module is to cover the workflow that we are going to take to Gain Access, Maintain Access and Covering Tracks. Footprinting, Scanning and Enumeration were about getting the big picture of the target. This module is about getting the big picture about the practical overflow we are going to use.
How do we do this?
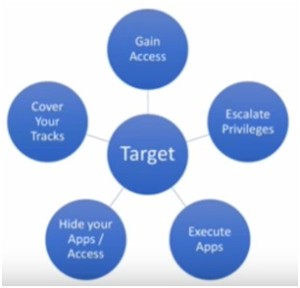
Figure 1. System Hacking
We start with the target. Now we have all the information about the target as we have collected it during reconnaissance and scanning phases. We will perform following tasks –
- Gain Access – We need to first of all gain access to the target environment. The following figure will make things clear –
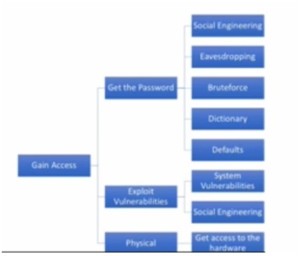
Figure 2. Gaining Access
- Escalate Privileges – Then we will have to escalate our privileges because if we have gained access as a normal user we will have to escalate our privileges as an administrator.
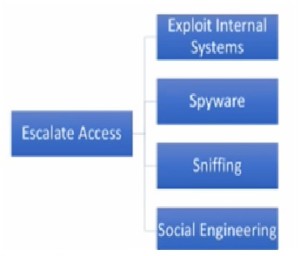
Figure 3. Escalate Privileges.
- Execute Apps – After this we want to execute our applications because we want to put key logger on the network. This we want to do backdoor so that we can gain access later on.
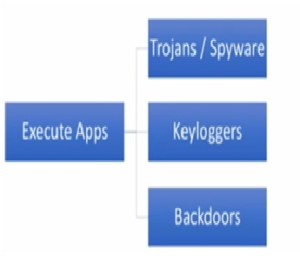
Figure 4. Execute Apps
- Hide Your Apps/ Access – We don’t want to be caught, so we need to hide our apps and access so that at a later point of time, we can get more data or change some system settings, etc.
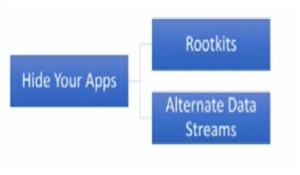
Figure 5. Hide Your Apps
- Cover Your Tracks – Finally we will cover our tracks to see that log files are clean and erase all the tracing that state that we were in the system.
Figure 6. Cover Your Tracks
What are the goals?
Our goals are to –
- Gain Access
- Exfiltration of data or Alter data
- Leave a backdoor
- Remove traces of your presence
What tools do we use?
We will use the following tools –
- Hydra
- Metaslpoit / Armitage
Ethical Hacking Tutorial – System Hacking Theory Video: