What is Cryptography?
Cryptography is practice and study of hiding information. In IT it is the practice of changing plain text into cypher text and vice versa.
What is Cryptography in the IT world?
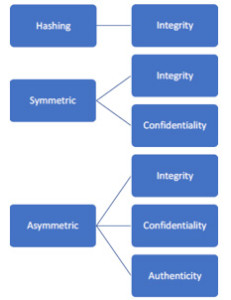
Figure1. Cryptography in the IT world.
Hashing – Hashing algorithms are used to verify that the data that is received is exactly the same as the one that is sent, etc. i.e. it is used to maintai
n the integrity of the data.
Symmetric – These algorithms are also used for integrity checking because a password is needed to change the integrity of the data. It is also used for confidentiality i.e. making something a secret by using encryption.
Asymmetric – It also has both integrity and confidentiality because it make sure that files don’t change and also encrypts the file but it also provides authenticity. It checks whether the person sending the file is actually the person or not.
What are Hashing Algorithms?
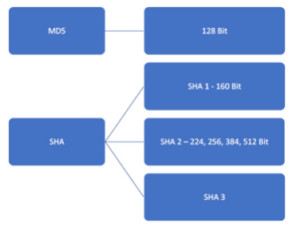
Figure2. Hashing Algorithms
MD5 – It is a 128 Bit hashing algorithm.
SHA – It is moreover a standard that comes with the following –
SHA 1 – 160 Bit
SHA 2 – 224, 256, 384, 512 Bit
SHA 3
The larger the algorithm i.e. the more the bit length or size, the more secure the hash is.
Symmetric Algorithms
The block size of an algorithm is the amount of bits or bytes that can be transformed by the block cipher. The key size is the number of bits in key used by the cryptographic algorithm. The longer the key, the more difficult it is to break it.
AES
Block Size: 128
Key Size: 128, 192, 256
DES
Block Size: 56
Key Size: 56 + 8 Parity – Parity to ensure communication integrity.
Triple DES
Block Size: 64
Key Size: 168, 112, 56
IDEA
Block Size: 64
Key Size: 128
CAST
Block Size: 64, 128
Key Size: 40 to 128 or 128,160, 192, 224, 256
2Fish
Block Size: 128
Key Size: 128, 192, 256
Blowfish
Block Size: 64
Key Size: 32 to 448
Serpent
Block Size: 128
Key Size: 128, 192, 256
Rijndael
Block Size: 128
Key Size: 128, 192, 256
Asymmetric Algorithms
They have two keys; one is public key which is known by everyone and private key which is only known by the owner.
Diffie-Hellman – It was the first asymmetric algorithm and was invented in 1976.
ElGamal – It was based on Diffie-Hellman.
DSA – Digital Signature Algorithm.
Elliptic Curve – It is a variation to DSA.
RSA – Rivest Shamir Adleman. It is most commonly used for both encryption and digital signatures.
Public Key Infrastructure
It uses asymmetric Algorithms so one must know thoroughly about them. They are used to create certificates for root Authority and normal certificate Authority. There are certificate authorities in the internet also e.g. Verisign, Godaddy, etc. who also verify the authenticity and then issue certificates. x.509 is the standard for certificates and it covers almost the whole public key infrastructure.
Ethical Hacking Tutorial: Cryptography Theory Video:
