What is SQL Injection?
SQL Injection is a web hacking technique used commonly to place malicious code in SQL statements. Most web applications connect to some sort of backend database, whether it is MySQL or Microsoft SQL or Oracle or any other. There are various kinds of database languages but databases and different databases speak derivatives of the same language. SQL Injection can be easily used to bypass a web application’s authorization and authentication mechanisms and retrieve the contents of an entire database. It can also be used to affect data integrity by adding, modifying and deleting records in a database.
SQL Injection : The Process with Example
The process of SQL Injection consist of the following steps –
Step 1 – Hijack Session
We are going to use an application called DVWA (Damn Vulnerable Web Application) to achieve our motive. For this first of all we will open DVWA in Firefox. Then enter the current IP address for e.g. 192.168.1.8. This will open login.php and now you have to login to the actual application by entering the username and password. We have logged in as admin. After logging in, set the security level to low so that SQL Injection can be done.
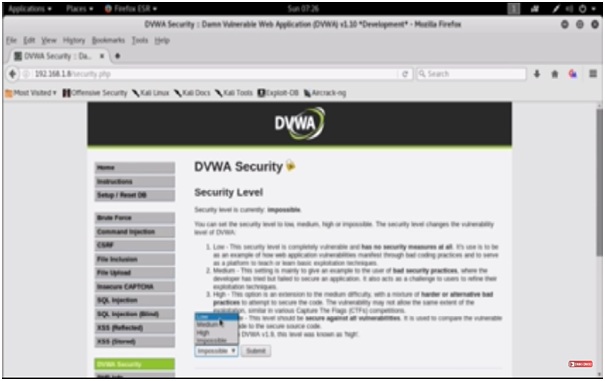
Figure 1. Security Level
Then we will go to the SQL Injection tab to start the session hijacking. There is a plugin called Tamper Data for Firefox, which can be used to get the network information. Once you have installed it, it actually captures the get and post requests as they are flying over the wire. This tool is specifically for HTTP and HTTPS traffic sniffing.
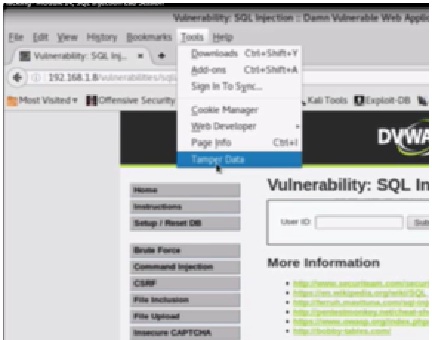
Figure 2. Using Tamper Data Tool
We will click on tamper data and then select start tampering.
As an example we will submit on ID no. 1 and click tamper. Now there is a tamper popup, we will click OK. As you can see ID 1 is admin.
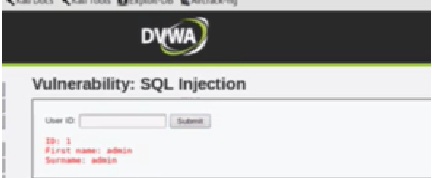
Figure 3. ID Details
Now we will click Tamper again and OK. Here we will get the GET requests. Now we will look for a specific cookie and the referrer. Because we need to do session hijacking, we have to be logged in to do it. We need the referrer to actually do the SQL Injection. So we will copy these and paste into a text document for further reference. After copying the text we will stop tampering.
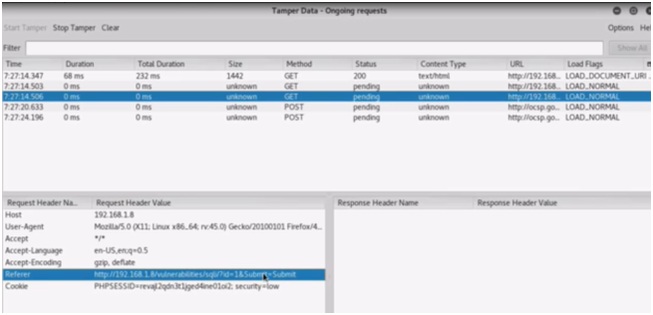
Figure 4. Referer and Cookie
Step 2. List Databases
Now we will start sqlmap and do SQL Injection. You can start sqlmap from command prompt. Open the shell and type sqlmap. You will get all the basic options. Sqlmap –hh can be used to get extended help.
First of all we will list the databases. The syntax for this is
Sqlmap –u “referrer” –cookie=”cookie” –dbs
In the referrer we will replace the referrer with the one we have copied earlier. Then replace cookie with the actual cookie. The command will look like this –
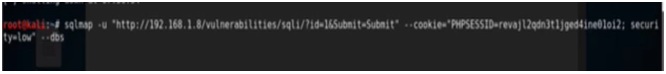
Figure 5. sqlmap cmd to List Databases
When we run this command, it will list all the databases on the database server. Now we will obtain the current database and the database user. The command will be –
Sqlmap –u “referrer” –cookie=”cookie” -b –current db –current user
Again replace the strings with actual values and run the command.
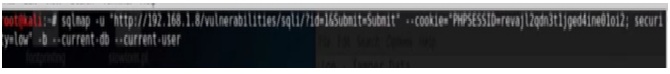
Figure 6. Get Current user and Database.
As you can see that in our example the current database is dvwa and the current user is dvwa@localhost.
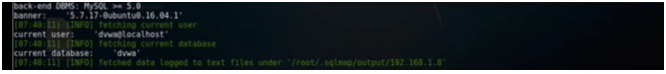
Figure 7. Current DB and User
Step 3 – Obtain Database Tables
As we know that the data actually resides in tables, so we will take out the table names to get the actual details. The command will be –
Sqlmap –u “referrer” –cookie=”cookie” –tables
It has given all the tables for all the databases. The best way to get only desired tables is specify the table with –D tag. Here our current database is dvwa so we will specify it.
Sqlmap –u “referrer” –cookie=”cookie” –D dvwa –tables
It will list all the tables of the dvwa database.
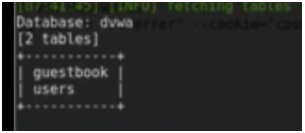
Figure 8. Tables
Step 4 – Obtain Database Table Columns
Now we are going to look at columns.
Sqlmap –u “referrer” –cookie=”cookie” –D dvwa –columns
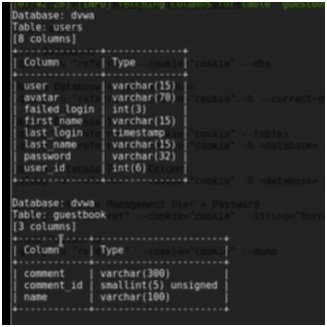
Figure 9. Columns
Step 5 – Obtain Database Management User and Password
Now we have got columns. Now we want the database management user and password. We will use the column name to get the info.
Sqlmap –u “referrer” –cookie=”cookie” –D dvwa –string=’Surname’ –users –password
This will give a warning and the passwords are not shown. So we can now use crack password script to get the details.
Sqlmap –u “referrer” –cookie=”cookie” –D dvwa — dump
Press yes for any warning. Here we get the username and passwords for all users.
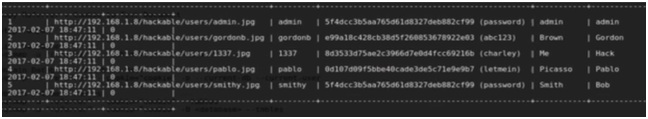
Figure 10. All User Names and Their Passwords
Step 6 – Use the info for SQL Injection
Now we will login with username Pablo to do SQL Injection. For this go back to Firefox and try logging with username Pablo. Now if you want to break this network go to SQL Injection and set the security to low. Now this user is completely vulnerable to SQL injection.
Ethical Hacking Tutorial: SQL Injection Lab Session Video: