For wireless hacking we will first of all put our wireless card into monitor mode and the command is –
airmon -ng start wlan0
We can check that it has been started by doing ifconfig. We are actually running this on a physical machine because not all wireless cards can be used for wireless hacking. So one should have the right hardware to do this.
airodump
The airodump command goes out and checks the network traffic. We will use the command –
airodump –ng wlan0mon
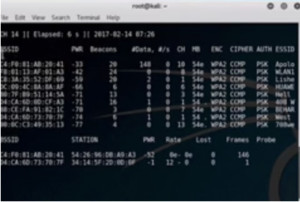
Figure1. airodump output
Here we can see the MAC addresses, the BSSIDs and other information of all the different WAPs in the region. Out of these we will attack WLAN1. For this we will isolate that. We will open another window and run the following command –
airodump -ng -c <channel> –bssid <bssid> -w dump1 wlan0mon
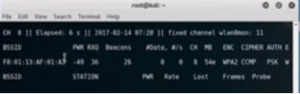
Figure2. airodump for wlan1
Now we are monitoring the one we want to crack. For demo purpose we will log on to the network using the iPhone. While logging we can see the handshake come through on the right hand side of the first line of our output. Now open up another terminal and do ‘ls’. It will show that there are dump files. These files are split into four files i.e. .cap, .csv, kismet and .netxml. We will run a crack on the dump to see if there are any handshakes.
aircrack -ng <filename>
We can see that there is no handshake. So now we will try to get a handshake to be activated on that card by logging in the network again. Now check the dump again. This time we have the handshake –
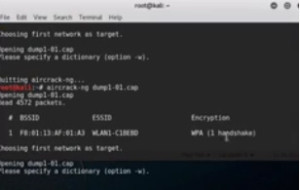
Figure3. aircrack output showing handshake
As it is WPA encryption we will use a dictionary. Here is the command –
aircrack -ng -w words.txt dump-01.cap
Here words.txt is the dictionary which has the key in it. The key is found –
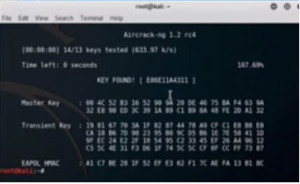
Figure4. aircrack key found
This shows that we have successfully cracked the network.
Ethical Hacking Tutorial – Wireless Lab Session Video:
