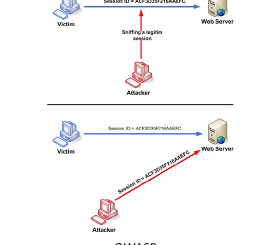
Symantec’s Internet Security Threats 2017
It is very well known today that the cyberspace became more dangerous in the previous year, 2016, with so many malware attacks all over the globe. Cyber criminals did huge operations which include even heist […]