What is Penetration Testing?
When we want to find the vulnerabilities of attack to a computer system, network or Web application, we use penetration testing. It is also referred to as pen testing. We can perform manual or automatic pen testing.
Why do we have Phases of Penetration Testing?
We have phases of pen testing so that we can follow a standardised methodology which can be rinsed and repeated over time so that we can look at information trends as well as reporting. This information can be used to compete to the penetration tests that other organizations of professionals have done. In other words it is setting a standard methodology to conduct penetration test.
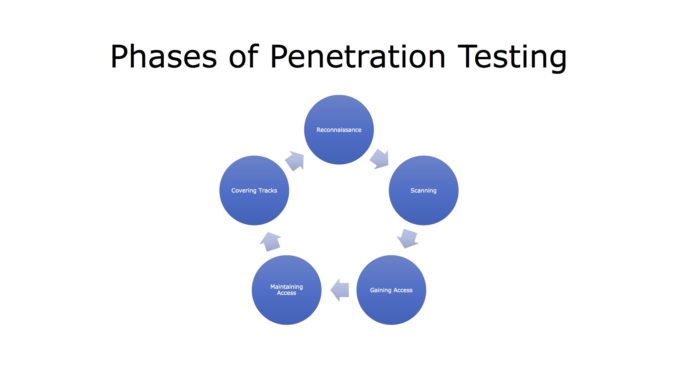
There are five phases of penetration testing –
- Reconnaissance
- Scanning
- Gaining Access
- Maintaining Access
- Covering Tracks
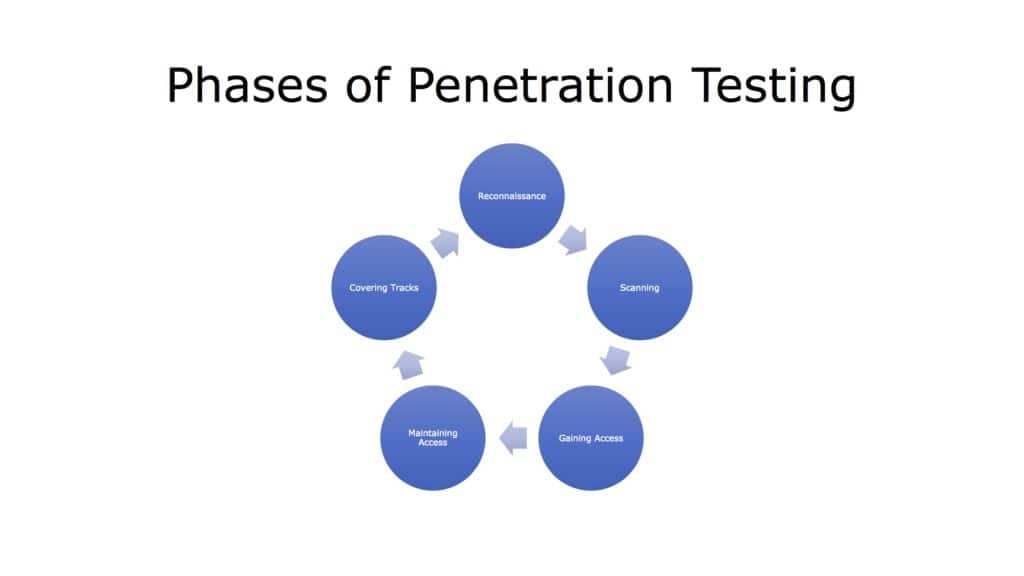
Fig 1. Phases of Penetration Testing
- Reconnaissance – It is the first phase of penetration testing framework. We use reconnaissance to gather preliminary data or intelligence on the target. The data is gathered in order to better plan for the attack. It can be performed actively or passively. By actively we mean actually touching the devices of the target. By passively we mean that your recon is being performed through an intermediary. In this we also perform things like identifying the target, finding the target IP address range, network, domain name, mail server, DNS records, etc. The tools which we can use in Kali server for reconnaissance are shown in the following figure –
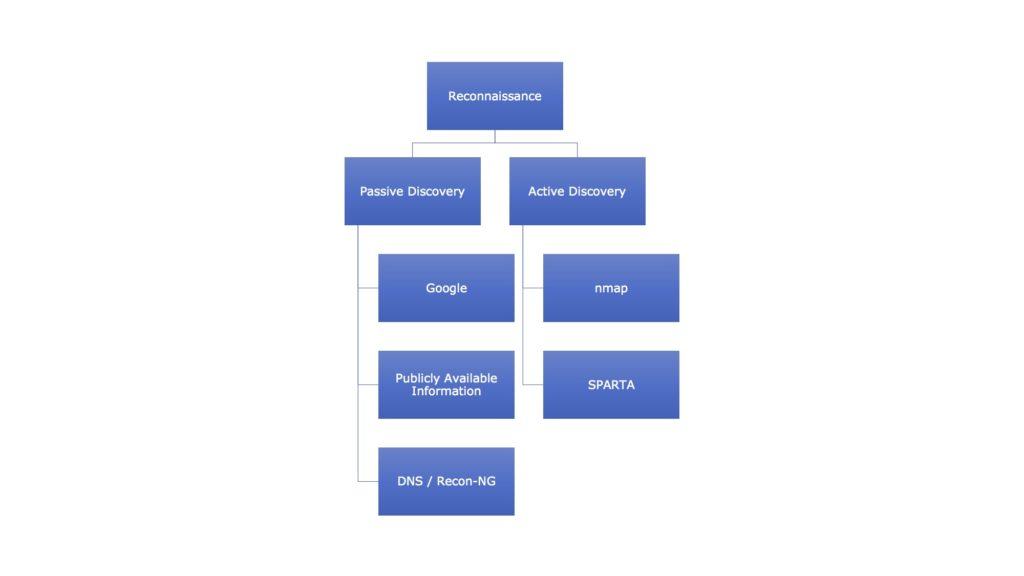
Figure 2. Reconnaissance Tools
- Scanning – The phase of scanning requires the application of technical tools to gather further intelligence on the target, but in this case, the intelligence being sought is more commonly about the systems that they have in place. A good example would be the use of a vulnerability scanner on a target network. There are some tools in Kali Linux for scanning also. These are shown in the figure –
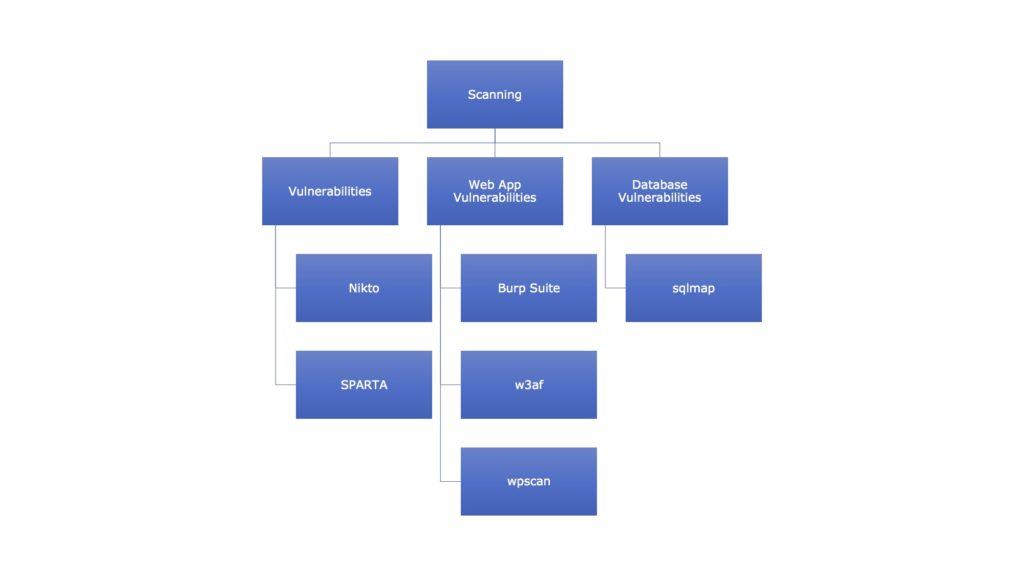
Figure 3. Scanning Tools
- Gaining Access – This phase requires taking control of one or more network devices in order to either extract data from the target, or to use that device to then launch attacks on other targets. The following are the tools in Kali Linux which help us in gaining access –
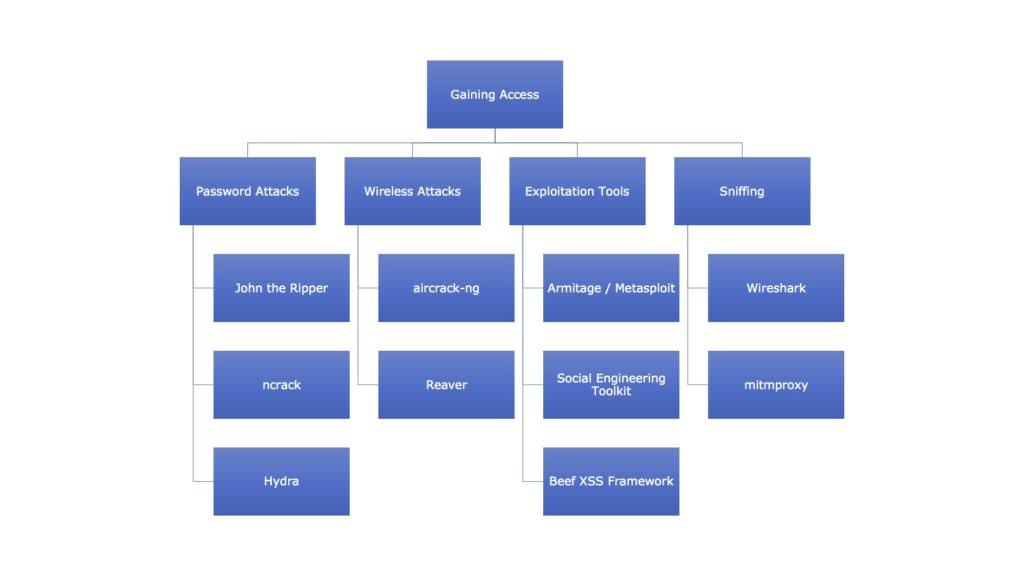
Figure 4. Gaining Access Tools
- Maintaining Access – Maintaining access requires taking the steps involved in being able to be persistently within the target environment in order to gather as much data as possible. The attacker must remain stealthy in this phase, so as to not get caught while using the host environment. It includes things like privilege escalation, back door installation on target machines so that one can maintain the gained access and connect to the target any time. The tools include –
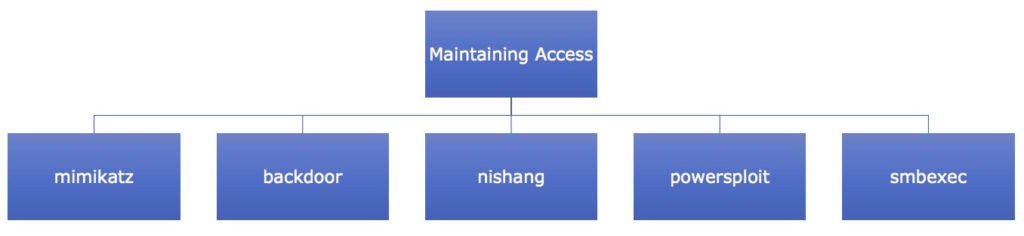
Figure 5. Maintaining Access Tools
- Covering Tracks – The final phase of covering tracks simply means that the attacker must take the steps necessary to remove all semblance of detection. Any changes that were made, authorizations that were escalated etc. all must return to a state of non-recognition by the host network’s administrators. The tools in Kali Linux that assist in hiding tracks are –
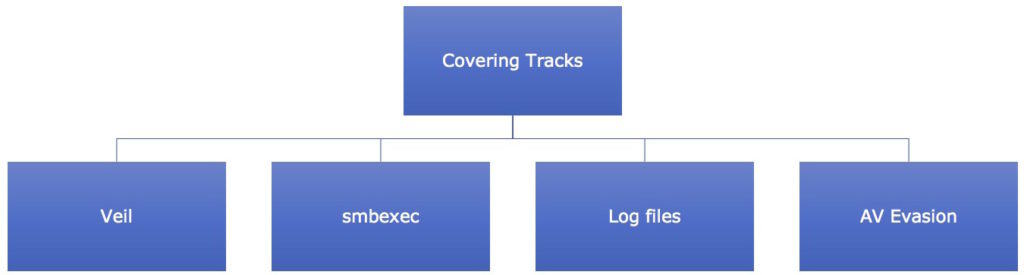
Figure 6. Covering Tracks Tools
Ethical Hacking Tutorial – Phases of Penetration Testing Theory Video: