What is Session Hijacking?
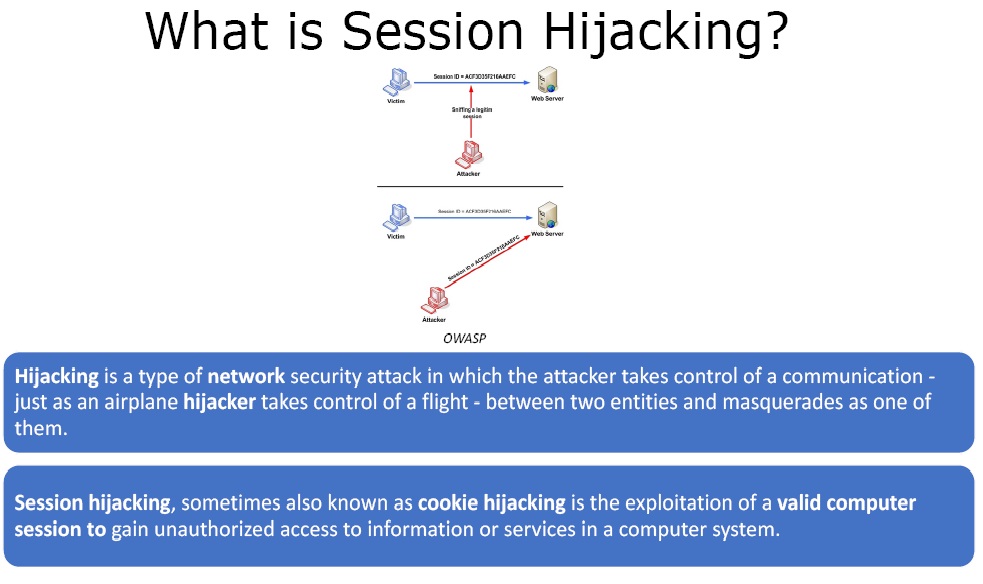 Figure 1. Session Hijacking
Figure 1. Session Hijacking
Hijacking is a type of network security attack in which the attacker takes control of a communication – just as an airplane hijacker takes control of a flight – between two entities and masquerades as one of them.
Session hijacking, sometimes also known as cookie hijacking is the exploitation of a valid computer session to gain unauthorized access to information or services in a computer system.
What causes a Session Hijacking Vulnerability?
Session hijacking could be a network session or any other session, but primarily it’s a web session. We will here concentrate on web session hijacking.
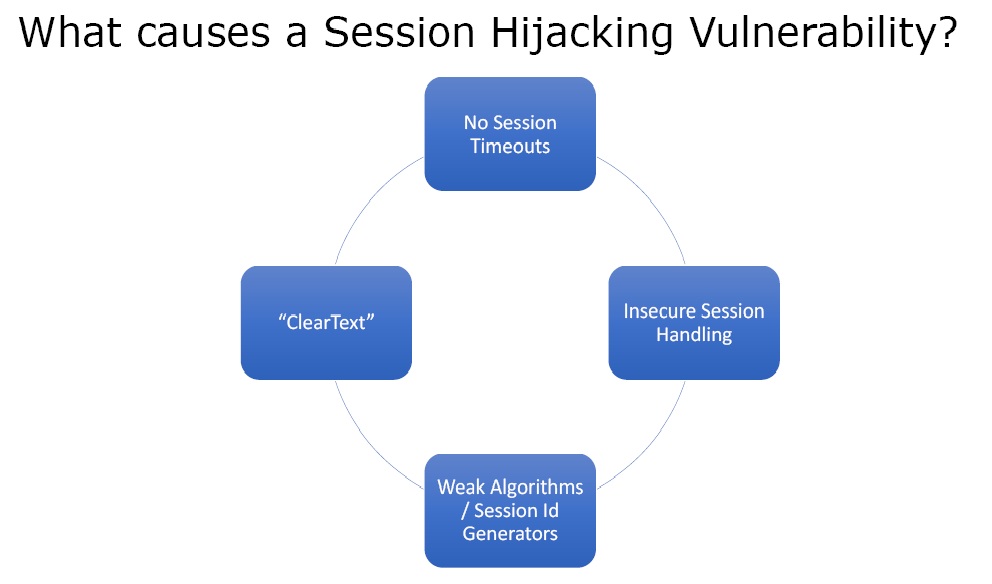 Figure 2. Session Hijacking Vulnerability
Figure 2. Session Hijacking Vulnerability
- No Session Timeouts – When we login to a website it creates a session state. This is done by creating cookies on the local file system by that website. This makes sure for e.g. in an email application that we don’t have to login again and again. But in secure applications like banking the session state should end after a certain timeout.
- Insecure Session Handling – It is based on how cookies are transmitted over wire and how they are stored.
- Weak Algorithms / Session Id Generators – If the session IDs are small and easily guessable, then session hijacking becomes quite easy.
- “ClearText” – If the tect is not encrypted it makes sniffing easy.
How are Sessions Hijacked?
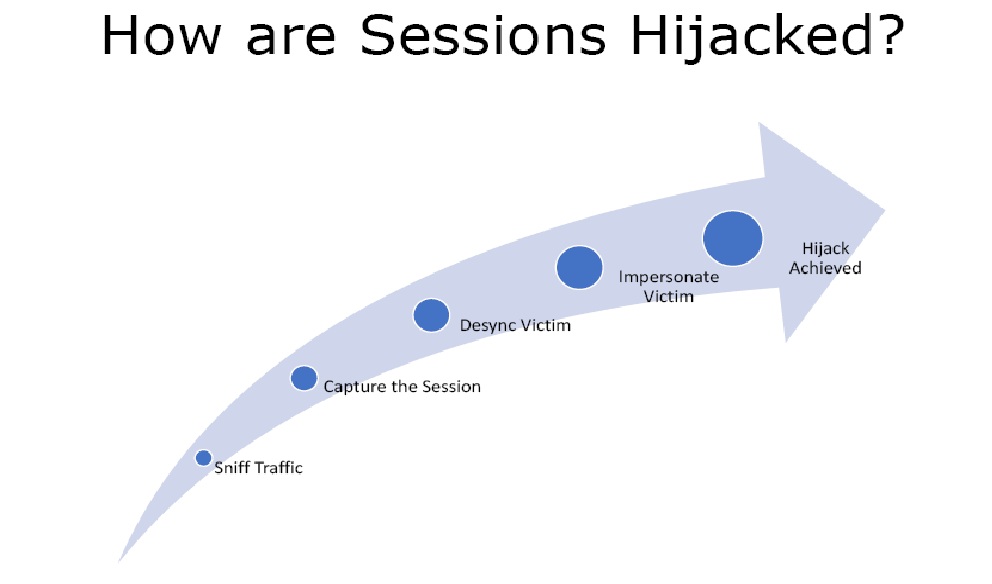 Figure 3. Session Hijack Process
Figure 3. Session Hijack Process
- Sniff Traffic – We have to perform man in the middle attack and be able to sniff network packets so that we can find unencrypted clear text cookies.
- Capture the Session – Capture the actual packet that has the cookie inside with the session ID.
- Desync Victim – In this we knock the victim offline and take over his session.
- Impersonate Victim – We take over the session of the victim.
- Finally the Hijack is achieved.
What are Session Hijacking Techniques
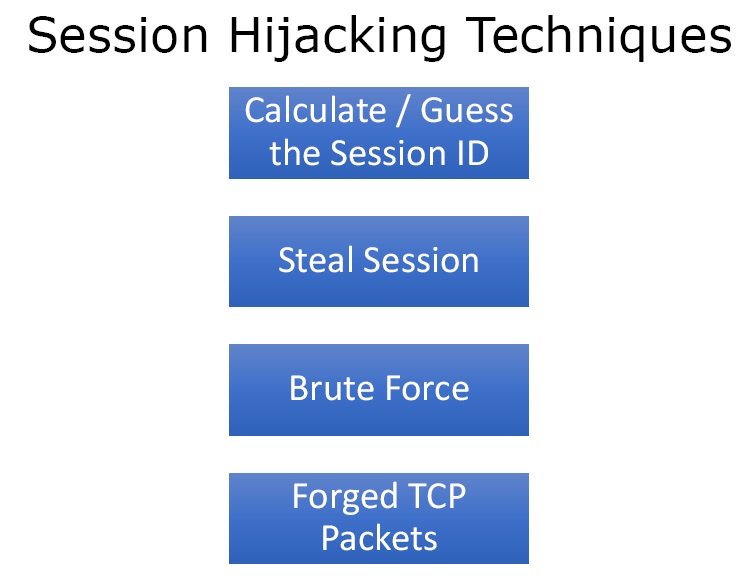 Figure 4. Techniques
Figure 4. Techniques
- Calculate / Guess the Session ID – If the algorithm is poor or one is just using consecutive numbers, it is easy to calculate or guess the session ID.
- Steal Session – In this we sniff the traffic and look for unencrypted cookie and steal the cookie and impersonate the user on the web application.
- Brute Force – If the session state is set to long time Session ID can be guessed and brute forced.
- Forged TCP Packets – Sessions on the TCP/IP stack are hijacked directly.
What are the countermeasures?
 Figure 5. Countermeasures
Figure 5. Countermeasures
- ENCRYPTION!!! – Encryption makes it difficult to sniff cookies and other packets on the network difficult to hijack.
- Random Number Generators – Very large random number generators could be used to create session IDs.
- Short Session State – The session cookie should be valid for a very short span of time.
- Principle of Least Privilege – Every user should only be given access to what they really need.
- 2 Factor Authentication – We can implement a second form of authentication to actually login to the system.
- Session Timeouts – If the session is not accessed for a particular amount of time and it has a short session state then the session should automatically end.
Ethical Hacking Tutorial – Session Hijacking Theory Video: