Man-in-the-middle-attack
The first thing we do in packet sniffing is initiate a man-in-the-middle attack so that all the traffic from the victim machine is routed through the attacker machine before it gets to the gateway. Here our attacker machine is Kali Linux and the victim is a Windows 10 virtual machine.
We will use some commands on Kali Linux to perform man-in-the-middle attack. First of all we will do
arp –a
This will give information about the arp table.

Figure1. arp output on Kali Linux
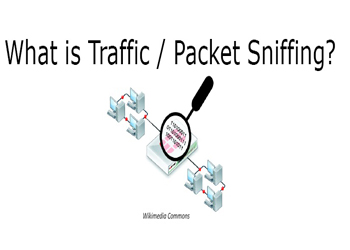
There is one entry for arp table and that is for default gateway and then is the MAC address of the default gateway. Now we will do the same i.e. arp –a on the Windows 10 machine.
Figure2. arp output on Windows 10
It has got the same default gateway and MAC address.
Start the Spoofing
The command we will use to start spoofing is –
arpspoof -i eth0 -t 192.168.1.100<TragetIP> 192.168.1.1<Default Gateway>
We can get the target IP address by doing ipconfig on the target machine. Run the command. It will start spoofing attack. Now we will do just the reverse in another window.
arpspoof -i eth0 -t 192.168.1.1 192.168.1.100
Now the spoofing attack is under way. Now if we see at the MAC address of the target machine by doing arp –a, we will see that the MAC address has changed that shows that sniffing is started.
driftnet
This is a Kali Linux command found in the menu itself, used to implement man-in-the-middle attack. Open drifnet and write the command –
drifnet -i eth0
This will open a small window of drifnet. Now if we try to run internet on Windows 10 machine, it won’t work because we must first enable IP40 as all traffic right now is ending at the Linux machine. Close drifnet. For this write the command –
sudo nano /proc/sys/net/ipv4/ip -forward
This will open a file. In this change the entry from 0 to 1. Open drifnet window again. Drifnet captures the images from the target machine.
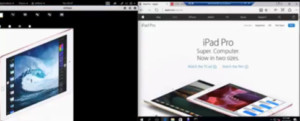
Figure3. drifnet output
Wireshark
It is a very good tool for packet sniffing. We can start it by typing ‘wireshark’ on the command prompt. Now choose the interface you want to listen on. We can already see the traffic flowing. There are a large number of filters we can use in Wireshark to filter the traffic. Here we will filter on 192.168.1.100.
Let’s perform password sniffing on Wireshark. Go to any website on the Windows 10 machine where you need to login with a username and password. Enter the details. Go to the wireshark window. Filter only HTTP traffic. Go to the post request and expand it.

Figure4. Password Sniffing using Wireshark
We can clearly see that it has literally sniffed the username and the password. We now know that sending clear text is very easy to sniff is one has initiated a man-in-the-middle attack.
Ethical Hacking Tutorial: Sniffing Traffic Lab Session Video:
