Every minute, an innocent internet surfer is the victim of malicious cyber-attacks, it for these reasons that internet security tips are essential. With infinite possibilities and unknown loopholes, the internet is wary to a plethora of attacks; one such being OS injection. Command injection refers to the process of a computer bug being manipulated to inject code into affected computer program that alters the course of execution. Operating system command injection is basically when an attack gets access to an operating system, which in turn means, OS command injection attack means the attacker can manipulate the system in two ways:
1) A malicious application that directly grants access to code manipulation. An application installed on the computer that allows the attacker to execute his own command via said application.
2) The application is used to run malicious software that allows the attacker to alter command; input is used by the application to select what program to run and what commands to execute.
Impact of Operating System Command Injection
Generally, an application that can be controlled via the web is said to be more vulnerable to command injection for it might pass sensitive information such as cookies, forms, HTTP headers to a user interface that grants access to the services of an operating system. The impact of such an attack can be widespread and disastrous. By having access to said application, the attack can manipulate commands to disclose sensitive information, additionally, by identifying inputs to affected operating system, it might also allow the attacker to execute commands that grant the attacker, even more, access and allow it to pass the security of said application.
By doing this the attacker not only gets access to top-secret information but might also lock access to important files as a means of negotiation. Unauthorized access to a system can have a greater impact than perceived, with this access the attacker can not only use the information for personal gain but might also sell this sensitive information to third parties, which has disastrous implications.
An example of one such instance is when an attacker uses time delay as a means of extracting information. In this situation, the attacker delays every command in order to identify what commands are executed successfully and which ones fail. The attacked then uses this information to find loopholes and inject commands that allow it further access to files. An attacker might input command that locks all files or steal information with intent to sell to malicious terrorist organizations.
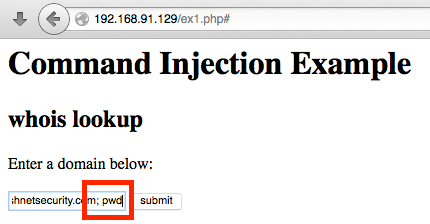
Example
For example, when an application intends on performing a DNS look up of a domain name supplied by the user, it is subject to the first variant of the OS command injection. Assuming the web developer did not take caution by validating the input of the user before classifying it as execute command, the attacker will be able to manipulate and run desired command on the server.
How to fix Operating System Command Injection
An attack on a computer’s Operating system can be prevented in a number of ways; the very simple one being steering clear of any websites that use redirection and pop-ups as a method of gaining access to one’s computer operating system and files.
Rigorous testing to gauge systems vulnerability had led to a number of following cyber security tips for this very common attack:
- Preventive measures work as prefix or such attacks. Specifying or white listing only known good values.
- Blocking access to script till the issue is resolved.
- Changing access permission for files.
- Another preventive measure is using an Application Programming Interface also known as API that separates parameters and commands. An API is a set of tools required to build software applications. It basically specifies how components of software should interact.
- Secure input and output handling
Recent attacks
Recently, an SQL command injection attack was blamed tied to an election commission breach. Every day, multinationals enterprises and banks are striving to protect their customers and their details. The year started with a bang when around 65,000 Airsoft GI accounts were leaked. This month alone a company called ‘Construction material online’ was fined after a command injection attack exposed customer payment details. Last month, 04/17, an attack led to patient’s prescription details being leaked. By far, the most interesting and remarkable one was on the famous anti-virus giant, McAfee; an attack that led to dangerous loopholes being found anti-virus central management suite. Our upcoming articles will also give you an insight into the latest mobile phone security tips.
Conclusion
Last year the Russian visa embassy was the target of a command injection attack. Day in, day out, financial institution and their tea of developers are fighting to make their code as strong as possible. Attackers looking for loopholes find a way to alter system command as a means of stealing classified information. They then use this information as a means of ransom and blackmailing. Access to customer information can also lead to money being stolen off bank accounts. It is an absolutely essential internet security tip for programmers to employ preventive measures as well as safeguards and loops within code and software to avoid such attacks. In an era where a human’s personal information is all but on click away, it is of utmost importance that this information be kept from manipulative hands that only seek to cause turmoil and harm.