Module 1.1 – OSI and TCP/IP Models
Two protocol architectures have served as the basis for the development of inter operable communications standards: the OSI reference model and the TCP/IP protocol suite. TCP/IP is the most widely used inter operable architecture and OSI has become the standard model for classifying communications functions.
What is TCP/IP Model?
TCP/IP is the result of protocol research and development conducted on the experimental packet-switched network, ARPANET, funded by the Defense Advanced Projects Agency (DARPA), and is generally referred to as the TCP/IP protocol suit. This protocol suite consists of a large collection of protocols that have been issued as Internet standards by the Internet Activities Board (IAB).
The TCP/IP protocol suite recognizes that the task of communications is too complex and too diverse to be accomplished be a single unit. Accordingly, the task is broken up into modules and entities that may communicate with peer entities in another system. One entity within a system provides services to other entities and, in turn, uses the services of other entities. Good software-design practice dictates that these entities be arranged in a modular and hierarchical fashion.
TCP/IP Protocol Stack
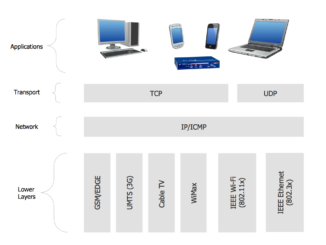
In order to provide flexibility in the implementation of protocols the approach of layered protocol stacks is used. TCP/IP model layers have different protocols. The layer at each level of stack is assigned a particular work and it communicates with other layers above and below it.
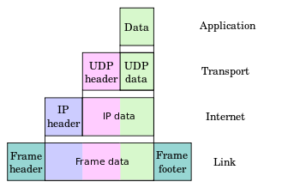
Fig. 1.1 – TCP/IP Model Layers
Here is the TCP/IP protocol stack –
- Application Layer – SMTP, FTP, HTTP, POP3, IMAP4, SNMP
- Host to Host or Transport Layer – TCP & UDP
- Internet Layer and Network Access Layer – IP
- Data Link and Physical Layer – Ethernet
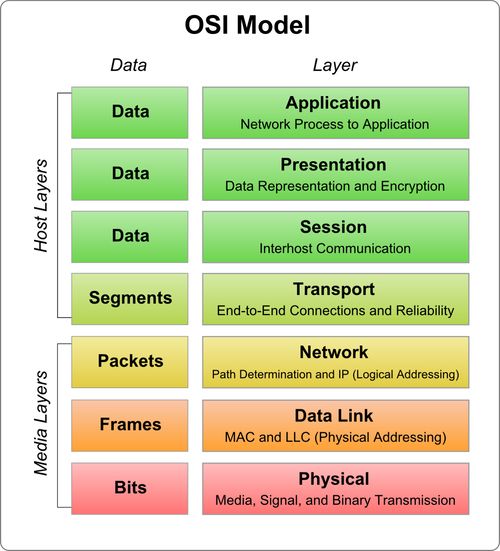
OSI Model Layers
- Physical Layer – At this layer the actual data transmission takes place. It deals with mechanical properties of the interface and also specifies the signal connectors i.e. circuits. It also represents the bits in terms of voltage levels. At this layer only the sequence of events is specified at which the bit streams are exchanged across the physical medium. At this layer, standards like EIA-232-E and parts of ISDN and LAN standards are used.
- Data Link Layer – This layer provides a more reliable connection and is responsible for providing means to activate, maintain and deactivate the link. It offer one most important service i.e. error detection and control. This way other layers can be sure about error free transmission once the data has left this layer. For indirect connections there may be various data links which are functioning independently and not relieving the higher layers of the responsibility of error control.
- Network Layer – Not everyone need to know about the data transmission and switching technology used to connect the systems. This layer relieves the higher layer of this and aids in the transmission of information between end systems. Here a dialogue is established between the computer systems to specify the destination address and work facilities like priority is also requested.
At this layer logical paths are created through switching and routing technologies in order to transfer data from node to node, known as virtual circuits.
- Transport Layer – When transport service is connection-oriented, this layer ensures that data is delivered in sequence, error-free and without duplication or no-losses. This layer ensures complete data transfer and may also perform the task of optimizing the use of network services. Here session entities may specify maximum delay, acceptable error rates and security and this layer will provide requested quality of service.
- Session Layer – Many a times there may be little or no need for session layer. But for some applications, this layer provides the mechanism to control the dialogue between applications in end systems. This layer is responsible for establishing two-way simultaneous (full duplex) or two way alternate (half-duplex) dialogue discipline. Here grouping can also be done by marking the flow of data to define groups of data. Here a checkpoint method can also be implemented for data recovery so that if at some checkpoint data delivery fails, the transmission can be restarted from that particular checkpoint.
- Presentation Layer – Presentation layer also sometimes known as syntax layer, defines the format of the data to be exchanged between applications. Data compression and encryption are some of the services that are performed at this layer.
- Application Layer – This layer acts as a medium for application programs to access the OSI environment. This layer performs application specific services including user authentication and privacy. Various general purpose applications such as e-mail, file transfer, Telnet, etc, resides at this layer.