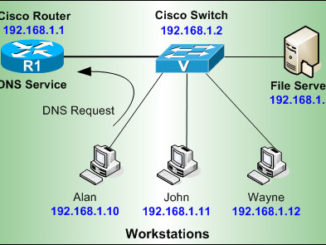
Here we will cover various protocols that allow distinct entities to communicate with each other over a communication network. These are a system of rules which define the message formats and describe authentication, error detection and correction, and signalling.
TCP/IP Suite
There is no official TCP/IP protocol model. However, it is useful to characterize the protocol suite as involving five layers. Although some implementations show TCP/IP model having 4 layers, here we have given a five layer model to be more precise. These layers are –
- Application Layer
- Host to Host or Transport Layer
- Internet Layer
- Network Access Layer
- Physical Layer
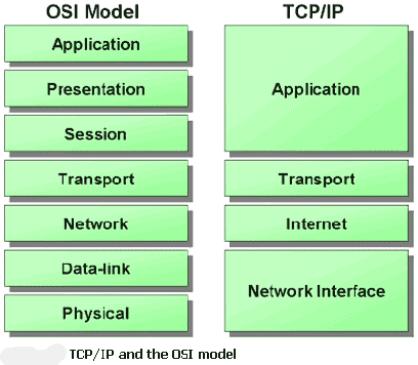
We will start from the lowest layer first.
- Physical Layer – The physical layer covers the physical interface between a data transmission device (e.g. workstation, computer) and a transmission medium or network. This layer is concerned with specifying the characteristics of the transmission medium, the nature of the signals, the data rate, and related matters.
- Network Access Layer – This layer is concerned with the exchange of data between an end system and the network to which it is attached. The sending computer must provide the network with the address of the destination computer, so that the network may route the data to the appropriate destination. The sending computer may wish to invoke certain services, such as priority, that may be provided by the network. The specific software used at this layer depends on the type of network to be used. Different standards have been developed for circuit switching, packet-switching (e.g. X.25), local area networks (e.g. Ethernet) and others. Thus, it makes sense to separate those functions having to do with network access into a separate layer.
When the data is to be routed between two end systems, which are attached to the same network, the network layer is used to provide access. When communication needs to be done between different networks, in order to traverse multiple interconnected networks, we need procedures. For this internet layer is used. To provide routing function at multiple layers, Internet Protocol (IP) is used. This protocol is implemented in end systems as well as in routers.
- Transport Layer – One of the requisite of data transmission is reliability. Despite of the nature of applications, that are exchanging data, the data should be exchanged reliability. We need to ensure that the data arrives in the same order in which it was sent. The mechanisms for providing reliability are essentially independent of the nature of the applications. Hence, all those mechanisms are collected at this common layer. This layer is also known as Host-to-host Layer. To provide this functionality, Transmission Control Protocol (TCP) is usually used.
- Application Layer – This layer contains the logic needed to support the various user applications. It provides communication between processes or application on separate hosts. For each different type of application, such as file transfer, a separate module is needed that is peculiar to that application.
TCP/IP is a critical area the knowledge of which is essential. You can go for TCP/IP certification to certify your skills in TCP/IP.
Communications Protocols
TCP
Two transport level protocols are included in the TCP/IP protocol suite i. e. TCP (Transmission Control Protocol) and UDP (User Datagram Protocol). It is used to create a connection between remote computers. It sends the data packets and ensures their delivery over supporting networks and the internet. IP and TCP works in collaboration with each other. IP defines the logical location of the remote node, and on the other hand TCP transports and makes sure that the data is delivered to the correct destination. TCP is designed to provide reliable communication between sending and receiving systems. TCP guarantees delivery of data and also guarantees that packets will be delivered in the same order in which they were sent.
TCP Header
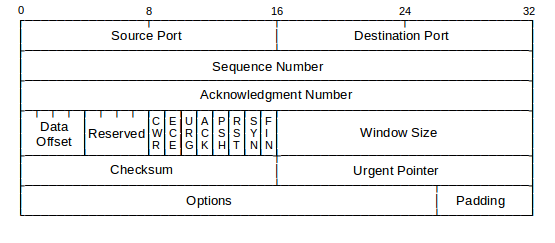
The minimum TCP header is 20 octets and maximum is 60. It has the following fields –
- Source Port (16-bits) – Source service access point.
- Destination Port (16-bits)- Destination service access point.
- Sequence Number (32-bits) – Sequence number of data bytes of a segment in a session.
- Acknowledgement Number (32-bits) – It works as acknowledgement of the previous data received. This number contains the next sequence number of the data byte expected.
- Data Offset (4-bits) – This field implies number of 32 bits in the header.
- Reserved (3-bits) – Reserved for future use.
- Flags (1-bit each)
- URG – Urgent pointer field significant
- ACK – Acknowledgement field significant.
- PSH – Push function.
- RST – Reset the connection.
- SYN – Synchronise the sequence numbers.
- FIN – No more data from sender.
- Windows Size(16 bits) – This field is used for flow control between two stations and indicates that. How much data is the receiver expecting.
- Checksum – This field contains the checksum of Header, Data and Pseudo Headers.
- Urgent Pointer (16 bits) – If flag is set to 1, tells how much urgent data is coming.
- Options (Variable) – Max segment size to be accepted.
UDP
For application level procedures, UPP (User Datagram Protocol) provides a connection less service. Therefore, in UDP delivery and duplicate protection of data packets is not ensured and hence it is unreliable. It seem to be adequate in some cases as the overhead is low. It does not provide congestion control mechanism.
UDP Header
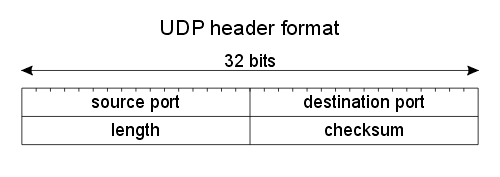
UDP header contains four main parameters:
- Source Port
- Destination Port– This is 16 bits information.
- Length – Length field specifies the entire length of UDP packet (including header
- Checksum– This field is optional.