
The first type of computer security attacks, we look at is:
Man in the Middle Attack in which the malicious person seeks to place a fictitious server between you or the system and the server you visit online. All communication between the system and server can be eavesdropped by the middle man.
Denial of Service Attack is the Denial of Service attack, in which the malicious person exhausts the available resources such that these are unavailable for the legitimate users.
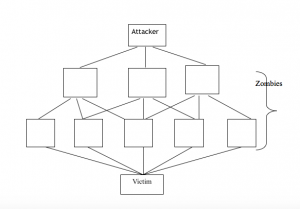
Distributed Denial of Service is the type of attack, in which the malicious person will distribute the attack over the multiple computers like 100s or 1000s of computer. These computers are not secure as the attacker plants in the what is called as Bot to overwhelm the victim.These computers who are involved in the attack do not know they attack and hence they are called as Zombies.
Spoofing refers to the electronic impersonation so the malicious person on the network can spoof IP address or MAC address. It is masquerading to be another person to gain access to a network or send a message out.
If computer B does not have an access to the internet, they will pretend to be computer A and use the internet. This is called as Spoofing.
This will lead to a numerous of attacks like Smurf Attack.
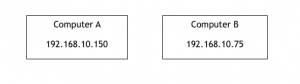 Spoofing
Spoofing
In Smurf Attack the computer A will spoof the IP address of computer B and flood a broadcast network with a Ping.This ping message will be sent out to all the machines on the broadcast network. Now at this time when computer B tries to access the machines on the network, they will reply to be unavailable.
Spam is another type of attack that are unsolicited mails. They have potential to load the servers and you run out of the servers.Some malicious users may send Spam by using the Instant Messengers called as IM’s. So if we have spam over social networks, it is called as SPIM.
SPAM+ IM= SPIM
