
In order to maintain security and prevent cyber attacks,the authentication services and authorization needs attention.
Under Remote Authentication Dial In User System (RADIUS), that allows for authenticating the remote users. It is often used in the dial up connection and enterprise grade wireless authentication setups. The RADIUS allows our users and authenticate them to connect with the internal network.
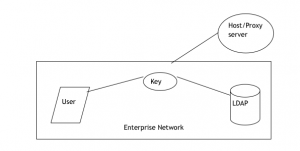
The authentication services facilitates username/password validation. It is installed as the virtual appliance and communicates with the local directory using LDAP over SSL.
Another way in which the user’s desktop is validated by Authentication Services, Desktop Single Sign On. These services are installed inside the LAN from where it acts as a federation server within your network. In case a user wishes to access an external URL, they are redirected to the Authentication services. From here the users are authenticated with the LDAP directory. The user credentials will never leave the corporate network.
The users can also use this mode from outside the network via a VPN connection.
Authentication deals with a process in which the credentials are compared with those that are already stored in the database on local operating systems or authentication server. If the two match the users are allowed to access. As soon as the users receive the permission they can judge their work environment, including hours of access and other rights such as the amount of allocated storage space.
The following part of the Module discusses the TACACS+.
TACACS + Protocol is the Terminal Access Controller Access Control System and RADIUS that have replaced the TACACS and XTACACS in the recently built updated network.
TACACS+ uses authentication, authorization,and accounting (AAA) architecture and TCP. It does not have to implement the transmission control as TCP is a connection oriented protocol.
In order to prevent the replay of credentials, we can have KERBEROS an authentication standard that employs key distribution centers (KDC) or Ticket Granting Service (TGS). These tickets are time stamped so that once they are presented to the servers, the servers able to track the use of tickets to prevent the replay attacks.The symmetric key cryptography was designed to provide Single Sign On where the users provide only one set of credentials to log on to every system they need access to which is supported by KERBEROS.
KERBEROS supports mutual authentication between users and systems. For Example: The banks use mutual authentication using an image where the users are authenticated to share the information.
LDAP Lightweight Directory Access Protocol enables anyone to locate organizations, individuals, and other resources such as files either on the public internet or on the corporate intranet. LDAP allows the users to search for an individual without knowing the exact location of the additional information.
LDAP is organized in a simple hierarchical format like that starts from :
The root directory which branches out to
Countries which branches out to
An Organization, which branches out to
Organizational Units like departments, divisions, and etc. which branch out to
Individuals that include people, files, and shared resources like printers.
