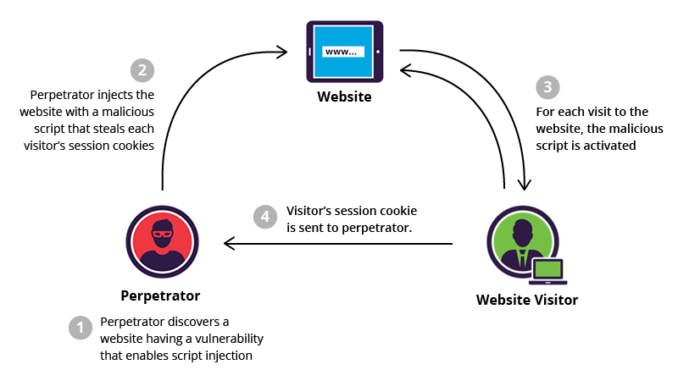
Cross site scripting Attacks (XSS) is a client side attack and it occurs if the applications doesn’t validate external input.
There are 3 types of Cross site scripting attacks:
- Reflected Cross site scripting: In this, a user enters some malicious input (javascript) into the application search box or some other feature which then produces the results including the user input and if the user input is not properly sanitized the javascript gets executed at the client side browser.
- Stored Cross Site Scripting: In this case when user enters some malicious input (javascript) into the feedback or contact form, the data gets stored into the database and this is later fetched from the database to see feedback or other details. As the value fetched from DB is malicious JavaScript, the script runs at the client side browser.
However, the difference between Reflected XSS and Stored XSS is that for the former one we need to form a request and trick the user to submit that request, but in the later one the malicious script is stored in DB and all users who have access to that particular DB value are affected.
- DOM based Cross site scripting: Here the user input (javascript) is not sent to the server side but is processed at the client side only and failure to sanitize data will result in execution of javascript at client browser.
Impact of Cross site scripting attack:
- A valid user session could be hijacked if the cookie attribute HTTPONLY is not set. HTTPONLY cookie attribute does not allow client side script to access cookie values.
- Website could be defaced, meaning website could be presented with unwanted textual descriptions and images.
- Malicious input stored in DB could alter the flow of the application when such data is used for processing etc.,
Prevention Techniques:
- Whitelist input validate data, this technique allows only trusted data to be entered into the application and avoids injection of any malicious data.
- In some cases applications are required to accept special characters and in such cases above prevention technique may not prevent cross site scripting. Hence, we may choose to output encode data which will prevent script execution(for ex: “<” is converted to “<” and “>” is converted to “>” thus it avoids execution of client side scripts).
- To prevent DOM XSS, consider to output the values into textual elements rather than html elements.Textual element such as inner.text=”value” and do not use inner.html=”value”.
there are many prevention techniques and it basically depends on the context of untrusted data utilisation. please refer to OWASP prevention cheat sheet for Cross site scripting online.