In this, first of all we will look at the default passwords. Open the browser, go to a search engine let’s say Google, and search for ‘default password lists’. We will find millions of results. Now if we open a link we will see that there is a huge list of default passwords with the manufacturer, the product, revision, protocol and default username and password. This shows that we should always change the default passwords as anyone can easily find it.
The following are the tools used for enumeration in Kali Linux –
- nbtscan
syntax: nbtscan <IP>
Open the terminal, type nbtscan and the IP let’s say 192.168.1.1-255. It quickly comes back with fully enumerated networks. It gives a lot of information much similar to scanning and also the machine name of the system.
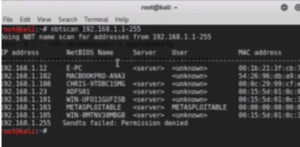
Figure1. nbtscan output
- nmblookup
syntax: nmblookup -A <IP>
It is used to lookup a specific machine. So here will for e.g. take 192.168.1.108 IP. It will enumerate the netbios for 108.
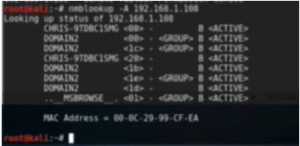
Figure2. nmblookup output
It can be very useful for looking up netbios on a specific windows machine.
- smbclient
syntax: smbclient -I <IP> -L <domain> -N –U “ “
Now we will try to connect to the same previous machine with smbclient. Here we will try to connect anonymously. This is possible only when the admin has not configured the server correctly and allow anonymous connections to the admin. In the command syntax, N is for username and U is for password.
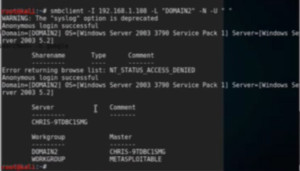
Figure3. smbclient output
The output clearly shows that it is now connected to a windows server and access is granted.
- rpcclient
rpcclient -U “ “ <IP>
enumdomusers + querydominfo
It performs the similar job as smbclient but gives proper domain information if it is connected. Once we enter the command it will prompt for password which shows that it has been protected properly. Here just to show we will connect with an authenticated Administrator account to show the information one can get with the null session be open to vulnerabilities. As we have the password, we are entering for demo purpose. We will get the rpcclient prompt.
Figure4. rpcclient login
Now we will run the command ‘enumdomusers’ to enumerate domain users.
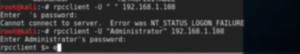
Figure5. enumdomusers
Next we will run ‘querydominfo’ to query the main information.
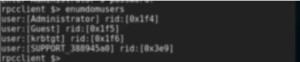
Figure6. querydominfo output
- theharvester
syntax: theharvester -d <domain> -l <number of searches> -b google
It is an information gathering tool. It is used for creating a domain information on Google or some other search engine. Here we are using the ‘Thundercloud’ domain but if you use it on a production domain you will get a large number of results. –l is for number of searches, and –b for search engine.
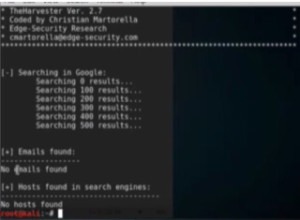
Figure7. theharvester output
Here we could not find anything. But if it would have found emails and hosts, it would have listed them in the respective sections.
You can also view the below video on Ethical Hacking Tutorial: Enumeration Lab Session:
