What is Enumeration?
Enumeration is the third phase of a penetration test. The ultimate purpose of enumeration is to get even more information about the target system and things such as routing tables, users or groups, etc. We have already seen that FootPrinting was about getting information, enumeration was about getting more information and enumeration is literally rounding up all of that information. Enumeration is active and does involve some scanning. This phase is about finalising the big picture and everything we will be doing in this phase will touch the target environment.
How do we do Enumeration?
We have a target and about that target we want to know a few things. Enumeration is there to finalise the big picture of all the information we gather about the target. We would like to know the things such as –
- Names – Server names, user names, network names, service names, etc.
- Services – What services are running in the environment like whether they are running Microsoft exchange for mail, or oracle or any other service?
- Network map – We want to get a network showing all the IP addresses and information about LAN and WAN.
- Users/ Groups – This makes the gaining access phase easier because if we have a username, we then have to get the password only.
- Routing information – To help build the network map.
- Operating Systems – List of OSs running on the target system.
- Passwords
- Applications running
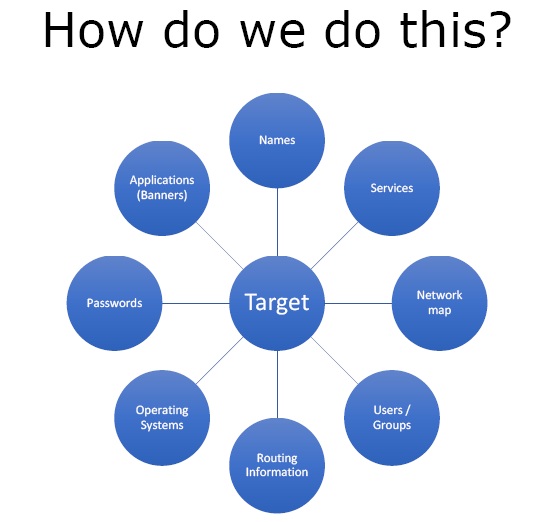
Figure 1 – What are we looking for?
Now we will have a look at how we start getting this information. We will have a look at protocols that give us information we want.
- NTP(Network Time Protocol)
- LDAP (AD) – Lightweight Directory Access Protocol (Active Directory)
- SMTP ( Simple Mail Transfer Protocol)
- NETBIOS
- SNMP (Simple Network Management Protocol)
- DNS ( Domain Name System)
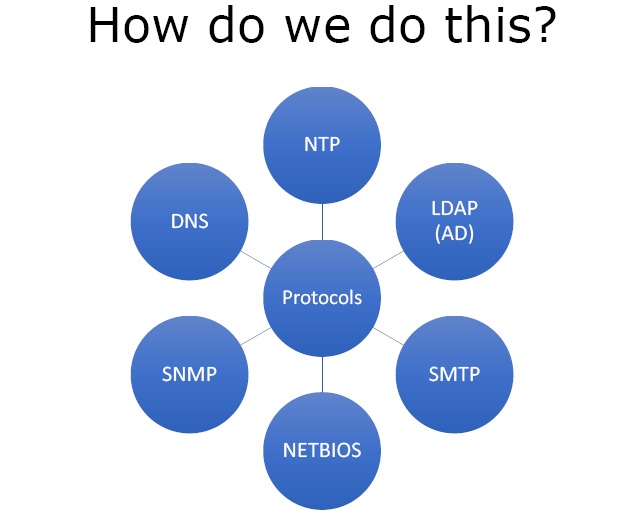
Figure 2 – Enumeration Protocols
Now we will look at the ports that we need to scan for –
- 53 – DNS
- 135 – Microsoft World Client-Server Communication Protocol
- 137 – NETBIOS browsing request port
- 139 , 445 – Common Internet File System
- 161 – SNMP, 162 – SNMP Trap
- 3368 – Global Catalog
- 389 – LDAP, 663 – LDAP over SSL
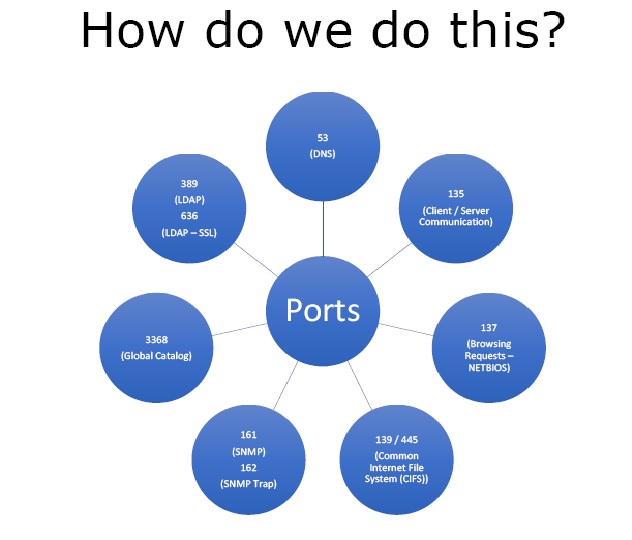
Figure 3. Ports
What are the goals of Enumeration?

- Finalise the details about the big picture.
- It also helps to finalise the path we will take to execute the attack in later phase.
- The information we ideally want at the end of this phase include –
- A list of devices and their roles and configurations.
- A network map – internal/ external/ wireless.
- A list of applications with version numbers.
- A list of people that work for or at the target.
Any information about the target no matter how insignificant it may seem could prove to be vital down the line. So we should collect and document everything.
What are the tools used in Enumeration?

- Default password lists
- smbclient and try to establish a Null Session
- netdiscover with macof
Ethical Hacking Tutorial – Enumeration Theory Video: