In the session we are going to use two Kali Linux tools to explain FootPrinting. The first tool is –
- DNS Recon – It is a tool for DNS reconnaissance. You will not find it in the Kali Linux tool list. In order to launch it, you must open a terminal and type dnsrecon. It will list the options available with the dnsrecon.
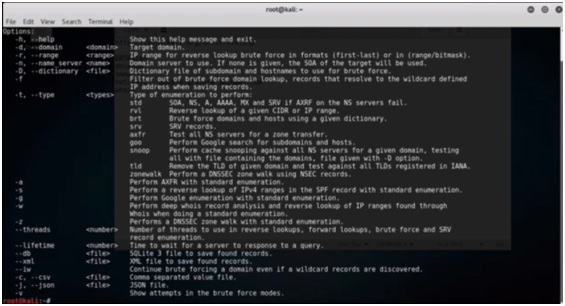
Figure 1. dnsrecon Options
Out of these we will use –D switch which is for domain which we will be FootPrinting and the –W switch which performs deep whois record analysis and reverse lookup of IP ranges found through Whois when doing a standard enumeration. So the command would be –
dnsrecon –d <domain> -w
Here the sample domain we have taken is thundercloud.co.za, so it will be replaced.
dnsrecon –d thundercloud.co.za -w
This is what we get –
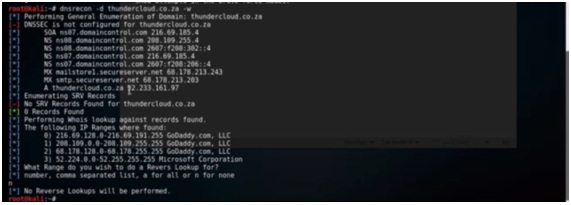
Figure 2. dnsrecon Output
We can clearly see that DNSSEC is not configured on this domain. We can also see that name service point to the domaincontrol.com with all the IP addresses. Here all MX records are also listed so we can query the mail server with these IP addresses. There is also a A record which might be a website. We can see that the first three IP ranges are registered to GoDaddy.com. The A record which we saw above of the 52 IP is in a block owned by Microsoft and that is because that web server is currently running on Microsoft’s cloud. The next thing it asked was reverse lookup which we have done not because it is more useful in internal penetration test because of the large volume of data.
- Dnsenum – It is also not listed in the Kali tools menu on the system. We will again open the command prompt and type ‘dnsenum’. We will get all the options. We will use this command to get all the subdomains using the –F key. Here we have taken some general subdomains which we can find against a specific domain that people have registered. The list can be vast but right now we will use this list for demo purpose. We have saved it in a file called subs.txt.
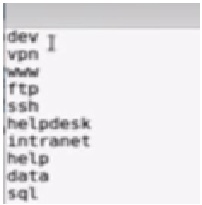
Figure 3. List of Subdomains
Now the command will be –
Dnsenum –F subs.txt thundercloud.co.za
In output we get that A record, we also get the nameservers, the two MX records. We also find some sub domains that points to possible servers and services running like dev and ftp. Here is the picture –
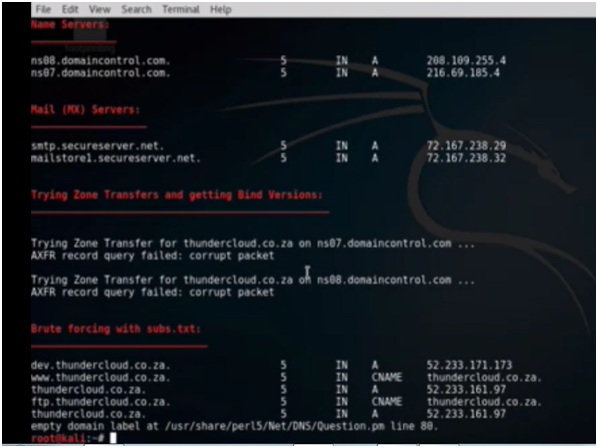
Figure 4. Subdomain Output
By now we have been doing passive reconnaissance as we have not actually creates any systems or services running on the target environment.
- Nmap – We will use this tool for doing some active reconnaissance. If we will type’nmap’ on the command prompt, it will show a number of options. We will use it to find a few open ports. The command is –
nmap -vv –p 21,22,80,443,1433,3306,3389 52.223.171.97
The numbers are different ports and we are going to test it for 97 IP. Here is the output –
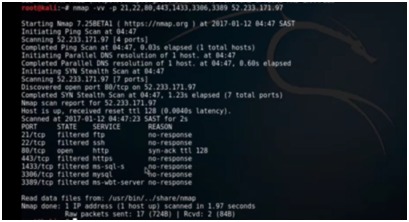
Figure 5. nmap Output
- Netcraft – Here we have come back to passive reconnaissance. Netcraft is a website and we will open it in the browser. Here we will find a section showing what’s that site running. This is a tool to find what technologies a website is running, its IP address and other important information about the website.
- Whois – It is mainly a registrar database. If we will google whois we will get a bunch of sites who does whois lookup. We will open the first link. For e.g. we can type Google.com to find out who actually registered Google. It will give a whole lot of information about Google.com which we can use for FootPrinting. With whois we can get a big picture of the domain.
Ethical Hacking Tutorial – Footprinting Lab Session Video: