What is FootPrinting?
It is the first phase of a penetration test. It is also called reconnaissance. It allows a hacker to gain information about the target system. In this segment, we are going to talk about Footprinting Theory like why we do it, goals and what are the tools used in it. FootPrinting can be both active or passive. By active FootPrinting we mean that we are creating devices or endpoints or systems and services within the target environment directly which can be logged. In passive we use publicly available information on the internet which actually often doesn’t even come close near the target environment.

FootPrinting is the process of accumulating data regarding a specific target for the purpose of finding ways to exploit the target in further phases.
Why do we do FootPrinting?
In order to perform or prevent an attack, we need to gather information and then look for weaknesses. FootPrinting is a very good mechanism to build a database of information about the prospective target which also helps in the reporting phase at the end of the penetration test. It shows the customer that how much information about their environment is publically available. We also use FootPrinting to learn about all aspects of perspective target’s security posture, systems, applications, people, suppliers, customers.

The more the information the more it is useful. So here we try to find out as much as possible without actually engaging the target. This holds actually true in the case of passive reconnaissance / FootPrinting because the customer is unaware that someone is actually interrogating its information.
What are the goals to FootPrinting?
The ultimate goal of FootPrinting is to get a holistic view and as much information as possible about the specific target. We do this so that we are able to set up the path that we will take to execute the attack in the later phase. For e.g. If the customer is not running an oracle system, then we will not try an oracle exploit during the penetration phase of the penetration test.

FootPrinting also helps to focus the energies in later phases on possible attack vectors. Now the question arise that what information do we ideally want at the end of this phase? The answer is –
- A list of devices and their roles and configurations.
- A network map – internal/external/wireless.
- A list of applications with version numbers.
- A list of people that work for/at the target.
We must remember that any information about the target no matter how significant it may seem could prove to be vital down the line.
What tools do we use?
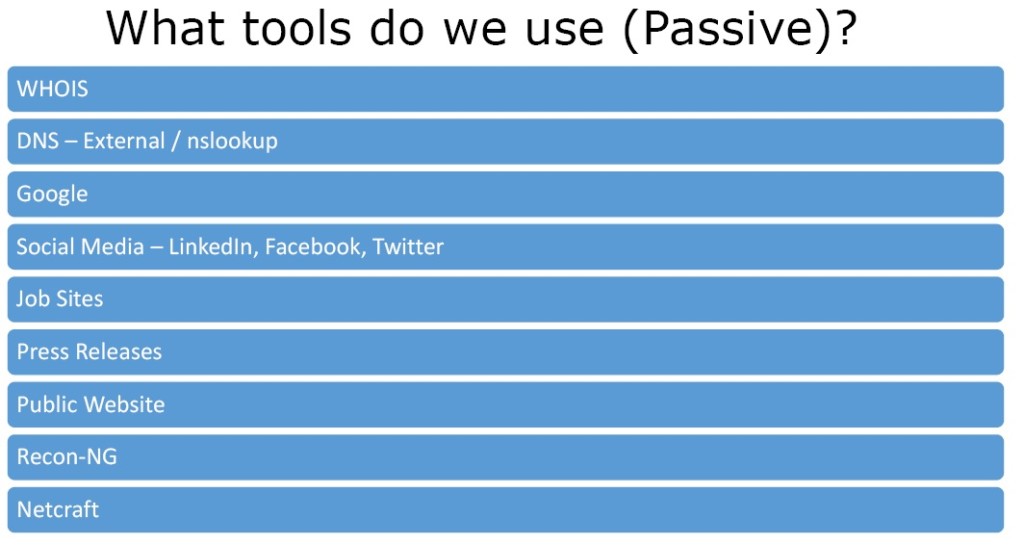
- FootPrinting WHOIS
- DNS – External / nslookup
- Social Media – LinkedIn, Facebook, Twitter
- Job Sites
- Press Releases
- Public Website
- Recon-NG
- Netcraft
Tools for Active Reconnaissance –
- DNS – Internal / nslookup
- Nmap
- SPARTA
- Internal Network Shares
- Public Facing Internal Sites – Webmail, VPN, Intranet etc.
One must always remember one thing that we are not doing this to exploit weaknesses. This phase is only about collecting information as much as possible about the target.
Ethical Hacking Tutorial – Footprinting Theory Video: