Cross-site Scripting Attack
Open a web-browser and go to a vulnerable website. We will here again use DVWA on IP 45.55.133.158. Log in and change the security setting to low. Go to XSS tab. On this website we have a sign the guestbook functionality.
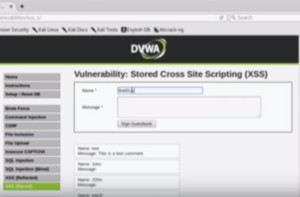
Figure1. DVWA XSS
For demo we will sign the guestbook as ‘BadGuy’. We will now embed a Java Script in the Message box. This shows that all untrusted data must always be validated otherwise this script will run in the browser. The script is –
<script> alert(“You have been hacked”) </script>
Now sign the guestbook. We can see that this alert pops up. Every time this page will load this alert will come. Here we have just created an alert but through Java Script one can do other things also like redirect to websites, download malware tool, etc.
Cookie Stealer using Cross-site Scripting
On the same page write the name ‘Badguy2’. In the message box write script –
<script> alert(document.cookie)</script>
With this we can collect all the cookies of people coming and steal the session ID. Now if we sign the guestbook now one more script will run and the message box will show the cookie with session ID and security level.
WordPress Brute Forcing
For demo purpose we have built a vulnerable WordPress site. We will see a web vulnerability scanner. In Kali Linux there is a scanner for WordPress i.e. WPScan. The command is –
Wpscan –url <url>
We will run this scan on our demo website. After the scan is complete we can see that it picks up large amount of information. This shows that WordPress with its themes and plugins can have vulnerabilities. With WPScan one can go to the references, find he exploit which are there in the exploit database and then using a tool like metasploit, go and attack it. in order to perform the attack we need users. The command for that is-
wpscan –url <url> –enumerate –u
It has given the users –
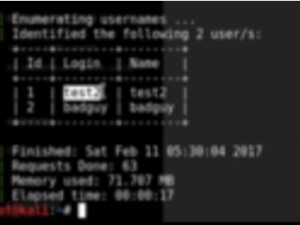
Figure2. Users on WordPress Website
Now we will perform a brute force attack on these two usernames. We have created a file with wordlist called sub.txt. The command for test2 user will be –
wpscan –url <url> –wordlist /root/sub.txt –username test2
After it has run we can see that it has successfully brute forced the password.
Hacking Web Application using Metasploit and Armitage
We will use metasploitable2 which can be downloaded from the internet and it comes in the form of a vmware virtual machine which we can then run on a vmware or convert it as per need.
Figure3. metasploitable2
Select the first app i.e. TWiki. We will see how to use Armitage to exploit this application. Go to Armitage, Add a host, with IP address 192.168.1.107. Right click the host and scan it. By the time it scans, we will go the Attacks menu and select Find Attacks. It will query all the exploits which we can see in the left pane under Unix->webapp. There are a number of hosts of web application exploits preloaded. We will use tricky_history from the list. Drag it to the host a dialog box will open, launch it. The command will complete and the host icon will change to red. Now we can interact with the shell. Now we can run all the commands like ifconfig, cd, ls, pwd, etc. as we have complete access to the root directory. We can bow go the files and make changes in them.
Ethical Hacking Tutorial: Hacking Web Applications Lab Session Video:
