For this demo we have a Kali Linux machine and an Ubuntu server running version 16.04.1. We will log in to the Ubuntu server and see that all the necessary updates have been done and the system is perfectly updated. But the web developer who deployed the web application on the server has left some loopholes. So we will compromise this web server.
Steps to Hack Web Server –
- We will get the IP address of the Ubuntu machine by doing ipconfig. Now on the Kali machine we open the IP in a web browser. We can see that it is running DVWA (Damn Vulnerable Web Application). We will log in to it and see that security setting is currently set to impossible.
- Now we will try to upload a file which will then create a backdoor on the server. But if directory transversal is off, then it will not work. On Kali Linux if we go to directory ‘/usr/share/webshells’ we see that there are a bunch of web shells that can be uploaded to a web server to compromise it.
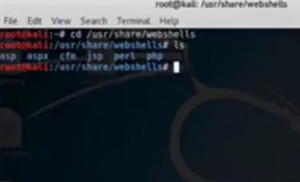
Figure1. Kali Linux Web Shells
DVWA is a PHP site so we do ‘cd php’ and get the listing with ‘ls’. We will use ‘simple-backdoor.php’ for the hacking purpose. We will copy it on desktop.
- Go to DVWA, browse ‘simple-backdoor.php’ and try to upload it. as per the validation of the application, it allows only images to be uploaded.
- Go to the security settings of DVWA app and set it to low. Now we will again go to file upload and browse the file again. This time the file has been successfully uploaded.
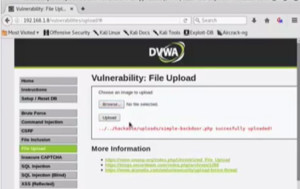
Figure2. DVWA File Upload
We can see that given the path where it has been uploaded or in other words the directory traversal is enabled.
- We can now go to the file system via the url. Copy the path and paste it in the address bar after the IP address. Here we can see the usage of the PHP script. It has given a command.
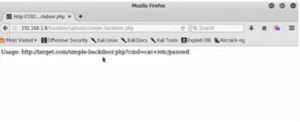
Figure3. PHP Script usage
- Copy and paste the command in the address bar and it will capture the etc/passwd file.
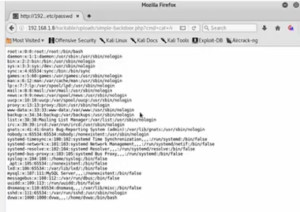
Figure4. PHP script command output
We can see that even on a totally hardened server we have a huge hole and are able to pull all the password file information. We can do ifconfig and see that we are actually on the server.
- We will make a directory with the command ‘mkdir test’. We can check if we have made the directory successfully by doing ls
- Now we will go to the server itself and do ‘cd /www/html’. This is where DVWA is installed. Now do ‘cd hackable’, then ‘cd uploads’ and then do a ‘ls –l’. We can see that there is simple-backdoor.ph and also the test directory. So from there we can create a user or do other tasks on the server that can give access to it and hack the web server.
Ethical Hacking Tutorial – Hacking Web Servers Lab Session Video:
