Welcome to third module of Ethical hacking course which discuss about Scanning theory. In our previous tutorial, we covered Footprinting Theory and now similarly we are going to talk about what is scanning, why we do scanning and what are the tools required to do scanning. Hope you will learn about Scanning in Ethical hacking from this module.
What is Scanning?
Scanning is the second phase of a penetration test. It allows a hacker to gain more information about the target system – port services, etc. Scanning is generally active that is why the chances of being discovered is more in this phase than in FootPrinting. FootPrinting also involves some scanning but this phase is about scanning only.
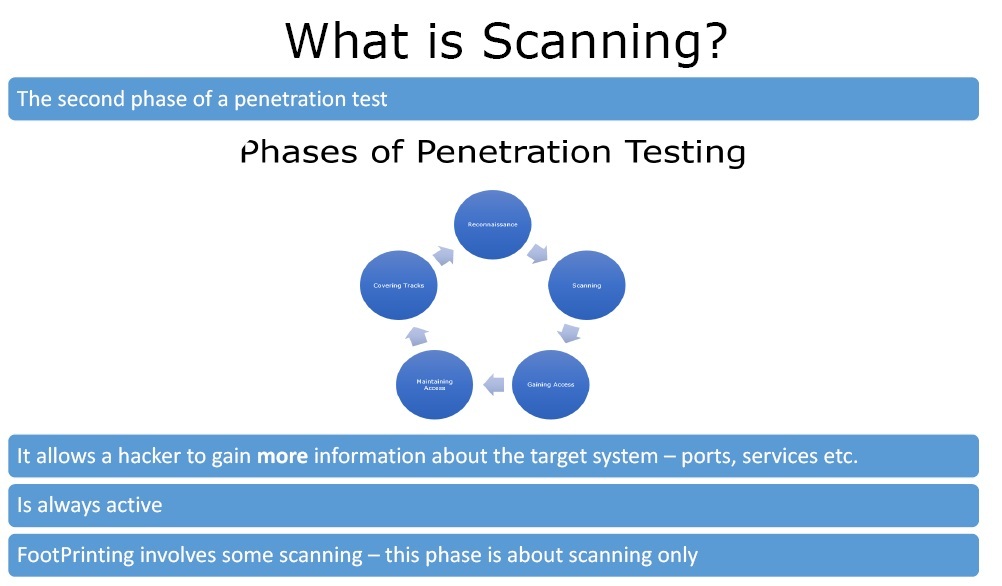
Scanning is one of the most important parts of intelligence gathering for an attacker. During the process of scanning, the attacker will try to gather information about the specific IP address.
How do we do scanning?
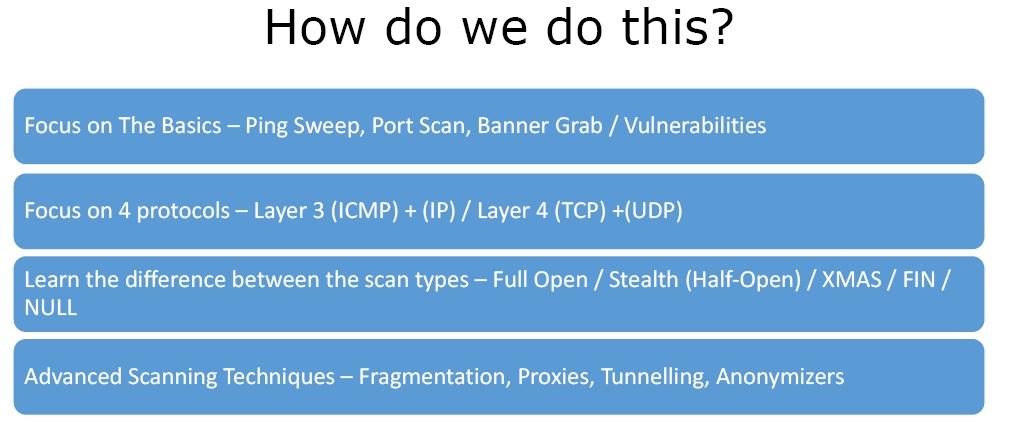
We first focus on the basics. The basics include Ping Sweep followed by Port Scan followed by Banner Grab or looking for vulnerabilities. We focus on 4 protocols in scanning. On the level 3 of OSI Model ICMP and IP, and at level 4 of OSI Model we look at TCP and UDP. A good penetration tester would know the difference and learn the following scan types –
- Full Open Scan
- Stealth (Half Open) Scan
- XMAS Scan
- FIN Scan
- NULL Scan
We also implement some advanced scanning techniques like fragmentation, Proxies, Tunnelling and Anonymizers.
What are the goals of Scanning?
- Get more detail about the Big Picture.
- We also use the scanning phase to refine the path we have setup in FootPrinting that we will take to execute the attack in later phase.

- The information we ideally want at the end of this phase include –
- A list of devices and their roles and configurations.
- A network map – internal/ external/ wireless.
- A list of applications with version numbers.
- A list of people that work for or at the target.
- Any information about the target no matter how insignificant it may seem could prove to be vital down the line. So we should collect and document everything.
What are the tools used in Scanning?
We will be using the following four tools in the scanning phase –
- nmap
- hping
- nikto
- nslookup
This phase is only about collecting more information than we did in the FootPrinting phase and it is not about exploiting any weakness that we find.
Ethical Hacking Tutorial – Scanning Theory Video: