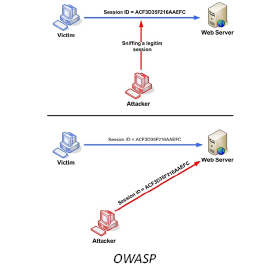
Man-in-the-middle Attack
We will start session hijacking with man-in-the-middle and start capturing packets. Here our attacker machine is Kali Linux and the victim is a Windows 10 virtual machine. First we will make sure that IPv4 is set to 1. To do this use command –
nano /proc/sys/net/ipv4/ip_forward
This will open a file. In this change the entry from 0 to 1. We will start spoofing with the command
arpspoof -i eth0 -t 192.168.1.104 192.168.1.1
We can get the target IP address by doing ipconfig on the target machine. Now we will do just the reverse in another window.
arpspoof -i eth0 -t 192.168.1.1 192.168.1.104
Now the spoofing attack is under way.
Wireshark Sniffing
Open Wireshark on the Kali machine. For this demo we have installed an application called DVWA( Damn Vulnerable Web App) on the Windows 10 virtual machine. it is a great tool when practising vulnerable web applications. Its home page will look like this –
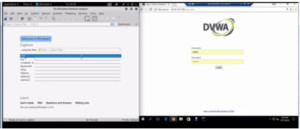
Figure1. Wireshark(Left-Kali Machine), DVWA (Right-Windows10)
Start capturing packets on Wireshark. Login with username and password in DVWA. Go to DVWA security, set the security level from impossible to low. Now we have captured the packets. Look at the cookies of this side by going into Chrome->More Tools->Developer Tools. Under application we can see cookies. There is the site with the session ID and security.
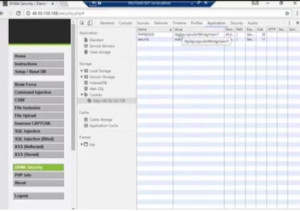
Figure2. Cookies
We will see if we have captured it on Wireshark also. We will stop capturing packets. Go to File->Save As… and save the actually captured file with .pcap extension on desktop.
We are going to use another tool called ‘Network Miner’ to actually look at the traffic. It takes a capture file and makes it readable. We can download the free version from Network Miner site. Follow the steps to install it on Kali Linux machine. It gets installed in opt directory. After installing, open terminal and cd into the Network Miner directory. Enter the command –
mono NetworkMiner.exe
Network Miner window will open. Go to File->Open and open the capture.pcap file. It will parse it and give all the information including IP addresses, files, messages, credentials, etc. We will go to the credentials tab.
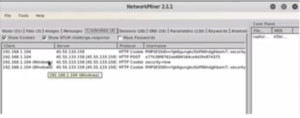
Figure3. Credentials
We can clearly see, that the Session ID has changed to security low. This is the session ID we need. We will copy it, paste it temporarily in a text document. We can see that they are two cookies and are exactly same as in DVWA.
Hijacking the Session
Open Firefox and open DVWA on kali machine also. We have a small Firefox plugin called ‘Cookie Manager Advanced’. Open that plugin and we can see some past cookies in it. We will delete all cookies from all domains. Now close it and reload the DVWA page. Open Cookie Manager Advanced again and click on the current session ID. Now we will change the Session ID to same as on the Windows 10 machine which we have copied on a text document. Also set the security to low and save it. Go to the same url i.e. 45.55.133.158/security.php. Now we have exactly the same access as we had on Windows machine.
Ethical Hacking Tutorial: Session Hijacking Lab Session Video:
