What is Social Engineering?
 Figure 1. Social Engineering
Figure 1. Social Engineering
Social Engineering is the use of deception to manipulate individuals onto divulging confidential or personal information that may be used for fraudulent purposes. This can be thought of ‘hacking’ into human nature.
How are the goals of Social Engineering?
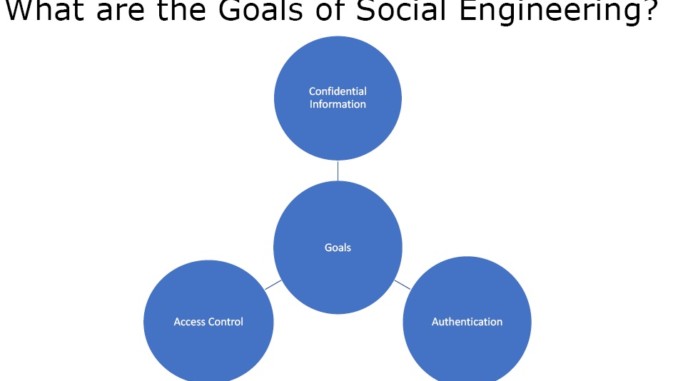 Figure 2. Goals of Social Engineering
Figure 2. Goals of Social Engineering
There are three primary goals in social Engineering –
- Get Confidential Information
- To get authentication Credentials
- Gain Access Control
So the main aim of social engineering is to get the confidential information and get information that we need down the line. It can be considered as extension of enumeration with a small aspect of gaining access.
What are the skills required?
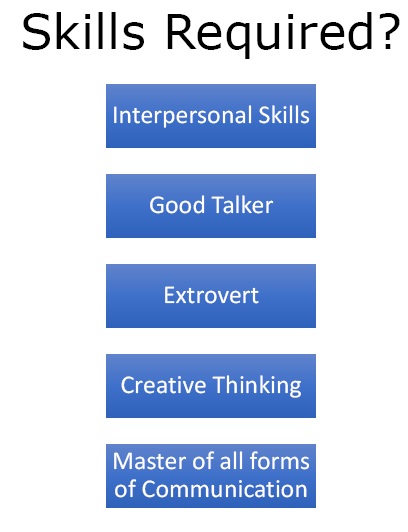 Figure 3. – Skills Required
Figure 3. – Skills Required
To be a good social engineer one needs to be an interpersonal skills person. One has to be a very good talker. He must be able to convince the target that he is what he is actually not so that they give username and passwords and confidential information and also access to secure systems. One must also have to be slightly extrovert to communicate effectively with people because this is for intensive purposes, the art of perception. Social engineering is thus an art as well as science. One have to think creatively as one needs to think up very clever ways to craft emails or check messages or phone calls to trick the target. These will convince the target to give the information or click on the link they should not click. In order to perform good social engineering, one has to be a master of all forms of communication as social engineering involves communication with the end users.
What Social Engineering Techniques do we use?
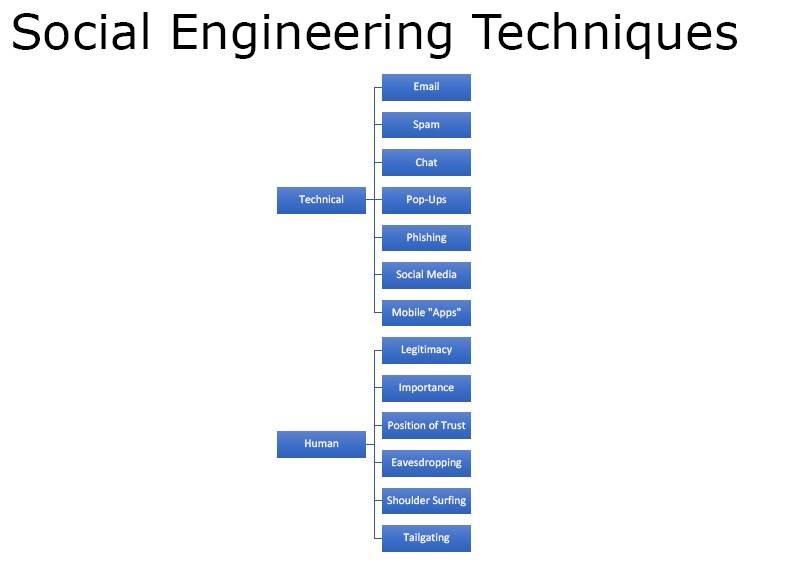 Figure 4. Social Engineering Techniques
Figure 4. Social Engineering Techniques
There are two major social engineering techniques –
- Technical
- Spam
- Chat
- Popups
- Phishing
- Social Media
- Mobile Apps
- Human – In this one has to be legitimate.
- Position of trust
- Eavesdropping
- Shoulder Surfing
- Tailgating
Why is Social Engineering so effective?
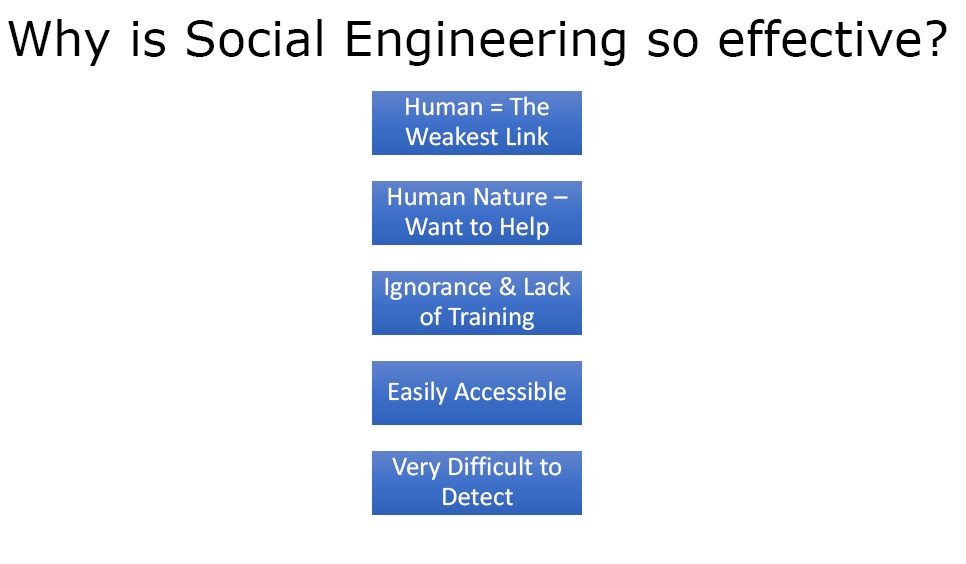 Figure 5. Why is SE so Effective?
Figure 5. Why is SE so Effective?
Social Engineering is one of the most effective techniques because it deals with humans. Humans are the weakest link in the security chain. It is human nature that everybody wants to help everybody else. So the hackers can take advantage of this and gain information. It also comes up as a result of ignorance and lack of training to the personnel in the organisation or to any other target. It is also easily accessible as one just have to walk up and start the conversation. It is also very effective because it is very difficult to detect.
What are the countermeasures?
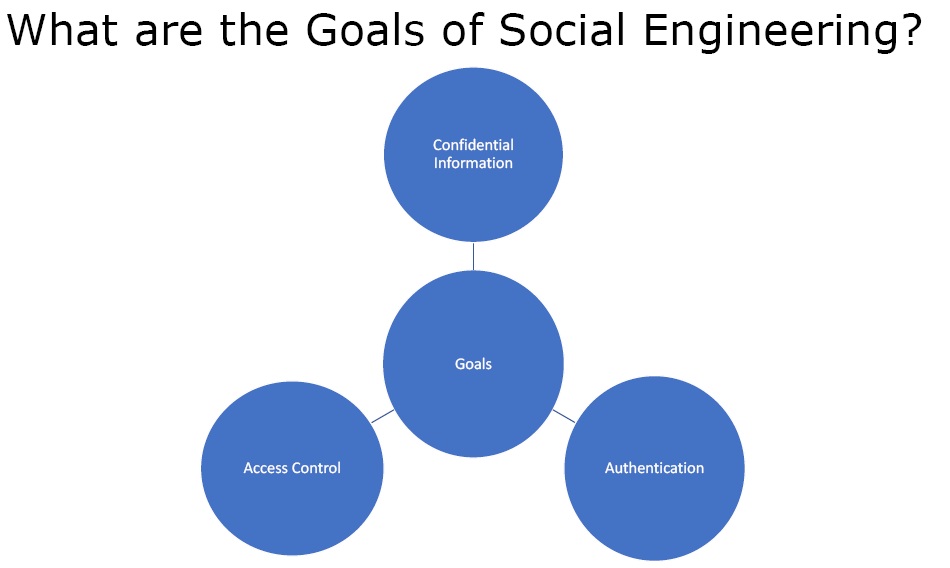 Figure 6. – Countermeasures
Figure 6. – Countermeasures
- Password Policies should be such that people change their passwords frequently.
- Account lockout should be implemented so that if somebody enters wrong username and password more than three times, his account is locked.
- User awareness training is a very powerful countermeasure which makes people aware about the risks.
- Classify and secure information i.e. not everyone has access to all the information.
- Escort visitors.
- Password reset best practices.
- Background checks for people one has employed or visit the organisation.
- 2 Factor Authentication with another protection apart from passwords.
- Anti-Malware for Phishing Attacks.
Ethical Hacking Tutorial – Social Engineering Theory Video: