This module of Ethical hacking tutorial will discuss about Trojans Theory which covers what exactly are Trojans, how to create it, how to detect them and countermeasures for Trojans.
What is Trojan?

A Trojan is a type of malware that is often disguised as legitimate software. Malware is a malicious software which performs something to the system which we actually don’t want to be done. Trojan is not always a virus. It is specifically a piece of malware that is disguised as legitimate software. It is an application that looks and acts exactly like it should, but inside the application is actually a piece of malicious code that is embedded in it and does something in the background.
How do we create Trojans?
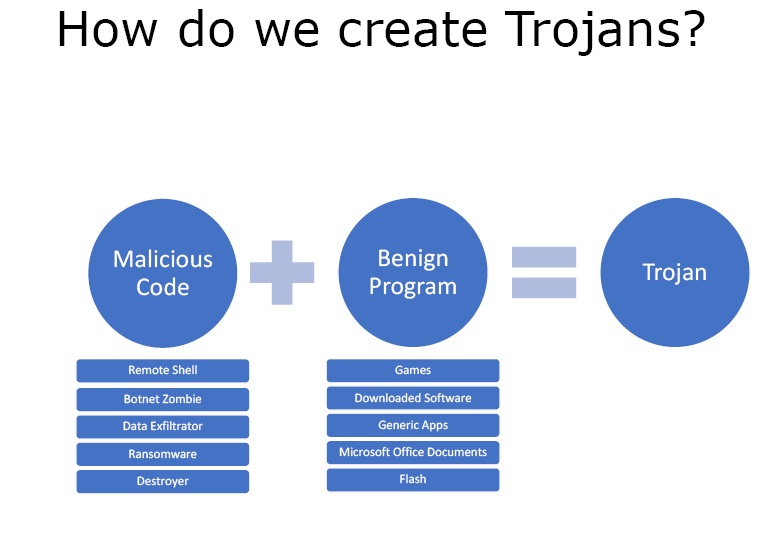
A Trojan is made up of two parts –
- Malicious Code – The things which we can do with the help of malicious code could be like-
- We can execute a remote shell so that we can have remote access to the device without the user knowing about it.
- We can make that system a botnet zombie.
- We can also use the code to exhilarate data of the network.
- It can be used as ransom ware also.
- We can use it as a destroyer to wipe the system files and cause havoc.
- Benign Program – The benign programs may contain Trojans like –
- Games
- Downloaded Software
- Generic Apps like calculator or notepad, etc.
- Microsoft Office Documents as they can execute VB Script if they are not protected.
- Adobe Flash is a vehicle to deliver Trojans into a network.
How do we detect Trojans?
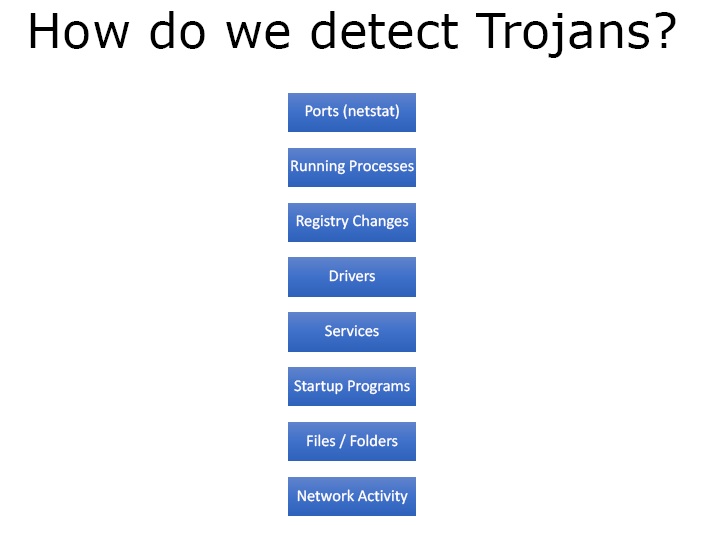
As an ethical hacker or penetration tested, we should know who is entering the system as we need to evade them later on. In order to detect Trojans we do the following –
- We look for open ports.
- We find running processes that are supposed to be on the target system.
- See the registry changes specifically in the windows environment.
- We look for any display or device drivers that are not supposed to be there but are loaded in the memory.
- We see that which services are running that are not supposed to be running.
- We also check the start-up programs when PC starts up in MS config.
- We check files and folders that there are any changes in the generic set of windows files and folders.
- Check for any anomalous network activity.
What are the countermeasures?
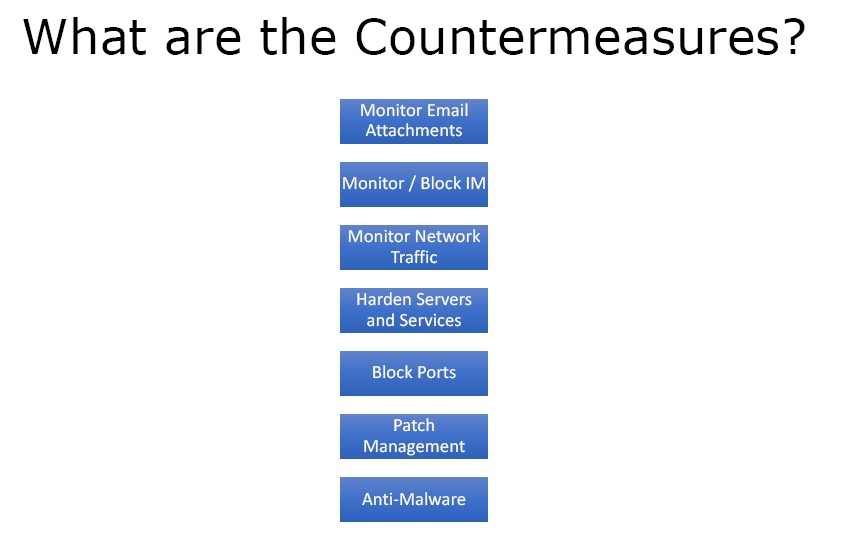
The countermeasures that IT department usually put in place includes –
- Monitoring email attachments and look for any malware by scanning the mail attachments.
- They monitor or block instant messaging because this is a popular way to get malicious code into a secure network.
- They monitor network traffic for any anomalous connections or weird IPs that are not supposed to be there.
- They harden servers and services and disable services that are not needed on the server.
- They block ports and allow only those which are needed so that one can control a lot more and prevent Trojans from making connections to any unspecified or abnormal port ranges.
- They patch their systems because a lot of Trojans take advantage of vulnerabilities in servers and services.
- They use anti malwares.
Ethical Hacking Tutorial – Trojans Theory Video: