While working with viruses and worms, there is a strong possibility that we ourselves get infected or cause a major outbreak. So, one should always work on either a virtual machine or a totally isolated system.
Downloading the Virus
There is website where we can find malwares. Go to https://github.com/ytisf. There you will find ‘theZoo’ which is a repository of live malware.
Figure1. Github.com
Go to malwares->Binaries. There is a whole list of malwares. They are helpful in practising malware analysis. Out of these for the demo purpose we will download ‘EquationGroup.Fanny’ malware. There is md5, sha256 and the password to open it. We will download the zip file and the password. But as soon as we complete the extraction of the file on the local system, windows defender will detect it as a malware and remove it. Open windows defender and allow access to this. Also disable antimalware. Now again extract the malware.
Malware Reverse Engineering
There is another tool on the internet named ‘virustotal’. It uses 57 different scanning engines from all the major anti-malware companies. If we upload our malware ‘EquationGroup.Fanny’ on it, it will give all the details about it. to get more information, one can go to the website and look for it in the virus encyclopaedia.
Malware Creation Kit
There are various such places on the internet where we can find malware creation kit. We will for our demo purpose use VX Heaven. This site is for educational purposes and we should also be ethical always while creating malware. On the VX Heaven website, go the constructors. We will search for ‘TeraBit’ as we will be using it to create a virus. Open the first link.
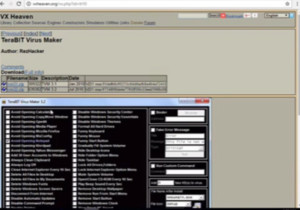
Figure2. VX Heaven TeraBit download
Now we will install the file by clicking on the second zip file. But as it is a malware the browser may refuse to download it. It can’t be downloaded in chrome, but Firefox gives an option to unblock such files. Download it and extract it to a folder. Windows may also show warning before running it but we will ignore it and run it on our system. Now it will open up.
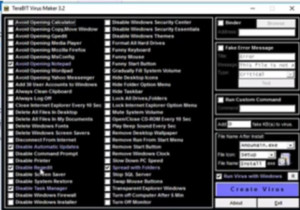
Figure3. TeraBit
We will leave all the default settings and create the virus. Windows defender may remove it as it is a virus, but we will allow this item from the defender history. Save it on the desktop and install it. as soon as it gets installed, all kind of weird stuffs start happening and the system will start behaving erratically. We can see it in the process explorer with a red and green line taking up all the memory.
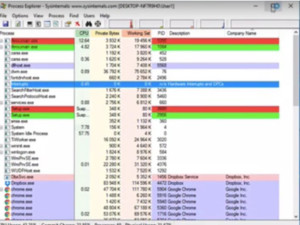
Figure4. Process Explorer
The machine seems to be very infected. Even if we try to kill the process it will deny access. We may have to take the machine off the network and clean it either by formatting it or through anti-malware. Here we can do this by enabling our real time protection. Windows defender will detect it and remove it immediately and system is back to normal.
One should be very careful while dealing with malware because they can also come with back door Trojans which are difficult to remove.
Ethical Hacking Tutorial: Viruses and Worms Lab Session Video:
