What is a Virus/ Worm?
A virus is a type of malware that is capable of replicating by reproducing itself and spreads by user’s action and typically has a detrimental effect. The major difference between a virus and Trojan is that a Trojan needs to be activated while a virus activates itself. A worm is a type of malware that is capable of replicating by reproducing and spreading itself without a user’s action and typically has a detrimental effect. In short we can say that a replicating engine and a payload collectively form a virus or a worm.
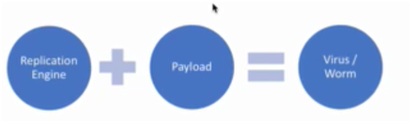
Figure 1. Virus/ Worm
How are Viruses/ Worms Created?
Computer virus kits generally create viruses and worms. We see different versions of the same viruses and that is because these kids make a little change ti the md5 hash of the original virus and create a new one.
Figure 2. Computer Virus Kit
What types of Viruses / Worms exist?
- Boot Sector – These are viruses that infect a boot sector of your windows PC. So when we boot up the system, it is already infected before we even login.
- File / Multi Partite – These are the viruses that exist in the file system and get activated when we click on a file or the file is executed by running a program.
- Macro – They run on Microsoft Office documents such as Word, Excel. When we run a macro, they run a VB script.
- Polymorphic – When we type any code, a polymorphic virus adds some code itself.
- Shell – They sits in the kernel or shell of the computer.
How are Viruses / Worms spread?

The following platforms are most vulnerable to viruses –
- Windows – The largest number of viruses are written for Windows OS. This is because over 90 per cent of PCs run windows so they spread widely in a faster manner.
- Android – Android is one of the largest OS on mobile systems so it is the second largest target for viruses.
- Mac OS
- Linux
- iOS
They are spread in the following ways –
- Malvertising – XSS – It is a combination of malware and advertising. There are various sites which people put with malwares and also some Adword run some JavaScript in the background and then attack the browser using cross-site scripting and infect the system.
- ClickJacking – In this when we click a link, it instead of taking to the page, also opens a popup in the background which also infects the system.
- Phishing – It is in the form of a attachment or a link.
- Open Networks – Especially open Wifi.
- App Stores – App can contain viruses.
- Software Download – Software may contain viruses so they must be scanned before installing.
What are the countermeasures?
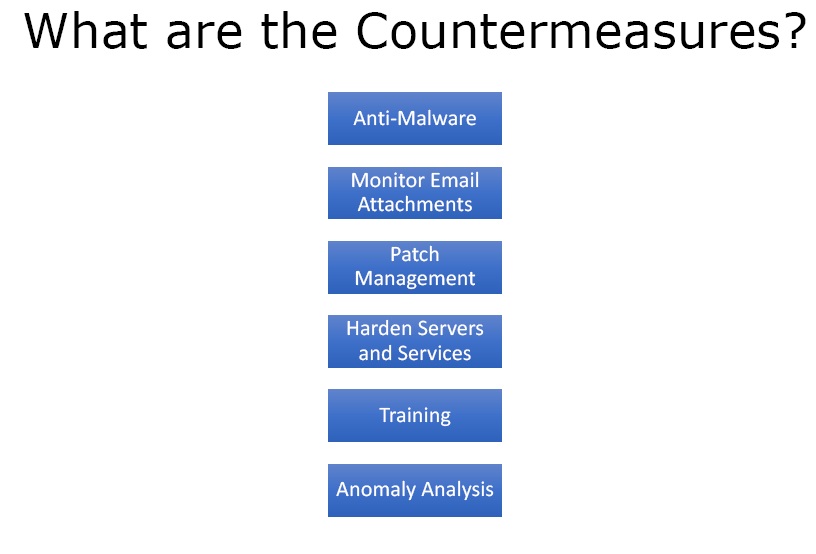
As a protector the following technologies and processes are needed to be used –
- Anti-Malware
- Monitor Email Attachments at both server and client levels.
- Patch Management
- Harden Servers and Services
- Training the users not to click links and download software that look malicious.
- Anomaly analysis.
Ethical Hacking Tutorial – Viruses and Worms Theory Video: