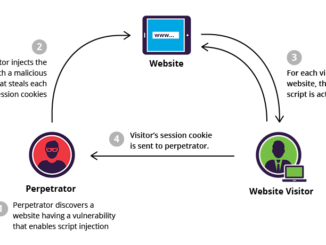
“SQL Injection“, the terms itself refer to one kind of attack. When attackers execute malicious SQL statements affecting your website or any web application, it is termed out SQL Injection. This is one of the most old and dangerous way to affect your web property.
When applications use SQL queries to interact with database contain direct user input without performing any validation then there is a possibility for SQL Injection as the applications fail to distinguish between sql code and data values.
Example query for SQL Injection:
SELECT username, password FROM users_table WHERE username = '" +userName +"' and password = '"+ password + "'For exampleifuser inputs' or'1'='1forboth usernameandpasswordfields in the above query then the interpreter will consider itassql code instead of dataandexecute sql queryasthe input 'or'1'='1 is always true.The above query changesasfollowing which is a true condition,gets executedandallows the user to login with privileges of firstuser account in the DB which is usually of an administrator.SELECT username, password FROM users_tableWHERE username =''or'1'='1'andpassword =''or'1'='1'
In this article we are going to discuss everything about SQL Injection which includes –
- SQL Injection types
- SQL Injection Test
- SQL Injection example
- SQL Injection Prevention
It is mainly classified into three types:
- InBand SQLi also known as Classic SQLi: In this technique the attacker uses same source such as a interface to launch the attack and also to gather the results.
There are two common types of inband SQL injection known as
Error based SQLi: In this technique a attacker tries to insert malicious payload and tries to get a error message which reveal sql related details and then understand it properly to frame a payload that can be used to exploit. For example an attacker may try to provide integer values where only string values are accepted which may cause an error.
union based SQLi: In this technique a attacker uses the UNION operator to combine the results of two or more SELECT statements and then return to client in response.
- Inferential SQLi also known as blind SQLi:
In this technique the attacker may take longer time to successfully exploit as it requires time to send in payloads and then observe the responses
There are two common types of inferential SQL injection
Time based SQLi: In this technique a attacker tries to inject a payload to get delayed response such as after a minute or so, based on the response the attacker can confirm the vulnerability.
Boolean based SQLi: In this technique a attackers tries to send payloads which send different results for a true condition and different results for false condition.
- Out of band SQLi: This technique can be used when an attacker cannot use the same source to launch an attack and to get results, in order to get this technique work there must be some settings that would have been enabled on the server.Hence, this is very rare type of attack.
SQL Injection Test : To test if your application is vulnerable to this attack you may hire a pentester who can try to attack your application and showcase the vulnerability or if you have the skill and well experienced you may use OWASP testing guide to check if your application is vulnerable. You will need to check at all pages where your application is interacting with database.
SQL Injection Prevention:
- Perform white list validation on end user data, do not trust any external input
- use prepared statements with bind variables to avoid injection of arbitrary data
- use stored procedures that do not construct dynamic sql queries
- use least privilege technique to avoid damage potential