
Cybersecurity remains the #1 corporate governance concern to date.
In fact, according to a recent report,
“2020 was the busiest year on record for cyberattacks.”
2020 observed the majority of businesses transitioning to remote work. Cybercriminals leveraged this opportunity, and some of the common attacks saw a significant rise.
Some cyberattacks are inevitable. It is imperative to follow critical cyber security tips to build a fence against the threats before they reach you.
Businesses Must Be well acquainted with the common cyber-attacks to stay proactively alert and avoid the expensive downtime and confidential data loss.
Here are 8 common cyberattacks we believe that you should be aware of.
Phishing Attack
Phishing is a widespread scam that every other internet user frequently encounters.
Cybercriminals convince users into believing that they are a legitimate company.
Big and familiar names like Apple, Netflix, and Yahoo are mainly spoofed by these bad actors.
Look at the phishing email below, which is supposedly from “Amazon” – again, a big name.
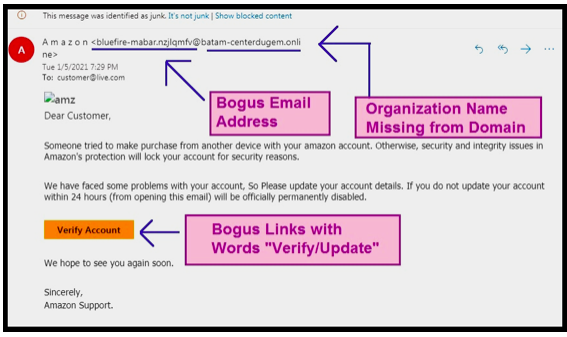
This is because unsuspecting consumers are more likely to give away (out of trust) their sensitive information, including payment credentials, to authoritative brands.
Fraudulent emails and messages are used to trap victims. These carry links that look very close to legitimate URLs.
But that’s exactly how you identify them.
No legitimate website will ask you for any sensitive personal information.
Look for a legitimate email, domain name, grammar mistakes, and emergency CTAs/ links to click on, if any.
2. Malware Attack
The term Malware is extracted from the original terminology “malicious software.”
Any software is malware software if it is intentionally designed to harm a system gain or unauthorized access to data from a device.
Organizations find Malware as the top security threat to date.
Before an organization prepares its system against one Malware, a new one is ready! In fact, over 350000 malware variants are caught in the AV-Tests per day.
Downloading an infected software/app/file/game from an unauthorized or dicey website is a source of Malware.
Once you install the malware-contaminated software, it self replicates and overwrites the existing files. It interferes with the system’s activities and slows it down.
3. Password Breach
What makes password breaching so common is the significant number of people using the same passwords for multiple sites. This is a terrible practice!
Hackers use a list of commonly used passwords to try multiple login attempts into employees’ accounts. Weak and easy-to-guess passwords are straightforward to crack.
In fact, compromised credentials used by employees account for 81% of data breaches.
Many companies, especially the banking sector, have employed biometric login to replace passwords. It actually provides an enhanced security barrier to hackers.
4. Man in the Middle Attack
‘Sophisticated threat actors’ successfully stole the Mimecast certificate issued to authenticate its products to Microsoft 365. How?
Mimecast fell prey to Man in the Middle attack.
A traffic interception made by an unauthorized party/ proxy (hacker) in a private communication between two people or applications is referred to as Man in the Middle (MitM) attack.
This attack relies on how easily a user can be fooled by a hacker when he (the hacker) impersonates one of the authorized parties involved in the conversation.
Financial and eCommerce entities are mainly targeted for MitM attacks.
Cyber actors can change and manipulate messages in transit as per their advantage. In the case of Mimecast, these actors compromised a device used in the network between user and server. With the stolen certificate, the hackers can easily connect to Microsoft and gain access to the user’s sensitive information.
5. Distributed Denial of Service (DDoS) Attacks
A Distributed Denial of Service (DDoS) attack is when many compromised computers are used to overwhelm a targeted website with data so that it crashes.
As a result, the website crashes down. It is unavailable whenever a legitimate user tries to access it because it is flooded with fake requests from these computers.
Then the attacker remotely controls all the infected computers.
Other resources like emails, networks, etc., are also prone to this threat.
One needs to keep track of the website traffic analytics, off traffic patterns, and an unusual surge in requests in a red flag pointing towards the DDoS cyber attack.
6. The Domain Name System (DNS) Tunneling Attack
The Internet has a phone directory – DNS. It has an IP address for each domain name.
Hackers misuse DNS for malicious purposes. They use it to establish command & control connections in a compromised device by channeling DNS requests to their own server.
Converting channels over DNS helps attackers bypass firewall filtering. DNS tunneling allows hackers to completely control the infected system or exfiltrate data from it.
7. Ransomware Attacks
It is challenging to recover a system from a ransomware attack.
Cybercriminals deny access to all the files to the victim by encrypting them. Victims are literally demanded to ‘pay a ransom,’ as the name of this attack suggests, to regain access to the files.
The victims are first manipulated using social engineering to click on malicious links or attachments.
Ransomware is the fastest-growing threat. One ransomware is due to take place every 11 seconds by 2021.
Companies have to safeguard their data against this potential threat by taking preventive measures.
8. Drive-by Download Attack
Cybercriminals use a Drive-by Download attack commonly to gain unauthorized access to a system.
It occurs when a user unintentionally downloads malicious software from an ill-intended website.
Why is it an unintentional download? Because the user is not seemingly clicking on a link to download anything. He simply views a page, and the download starts in the background – now you know why it is termed as a “Drive-by” download attack.
Final Takeaway
Any risk amongst these can pose a more significant threat to your business. Watch out for all of these cyber threats.
With hackers getting smarter and hands-on with their techniques, you need to stay aware of the updated and common cybersecurity issues.
It is highly recommended to seek an IT cybersecurity team to monitor your networks 24/7 and assess your security needs.
