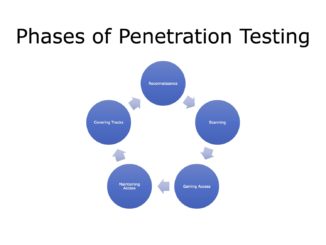
Ethical Hacking Course: Phases Of Penetration Testing
What is Penetration Testing? When we want to find the vulnerabilities of attack to a computer system, network or Web application, we use penetration testing. It is also referred to as pen testing. We can […]