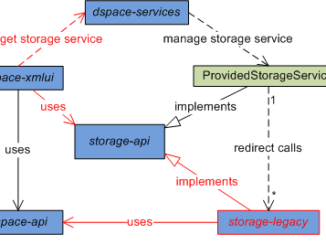
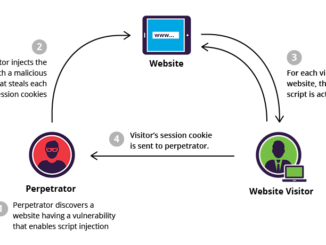
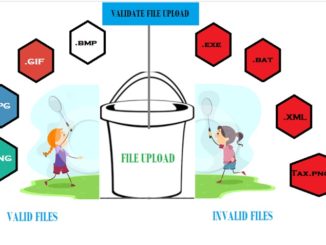
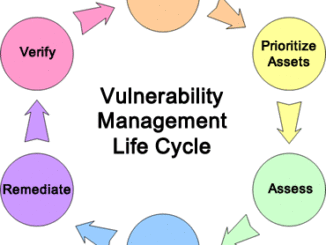
Everything About SQL Injection In Database And Prevention
“SQL Injection“, the terms itself refer to one kind of attack. When attackers execute malicious SQL statements affecting your website or any web application, it is termed out SQL Injection. This is one of the most […]