Web Application Attacks
Increasing attack surface – Subdomain Discovery Techniques
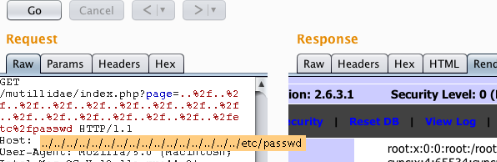
The crucial phase of attacking an application is in reconnaissance or information gathering. The more info we have at hand the more are the chances of getting successful with attacks or exploits. The one useful [...]