In this lesson, we will teach you all you need to know about file traversal attacks. Of course, we will start from the beginning, understand this issue, then, later on, we will learn how to recognize it, and in the end, how to fix or even better, to prevent it! So, I won’t take any more of your time, let’s start exploring this issue together now!
File Path Traversal Description
These vulnerabilities mostly arise once when the user’s data which should be controllable are used within some of the file system operations and all that in the unsafe matter. What happens here is that the user himself provides his supplied filename which is already appended to the certain directory prefix. It has to be done that way because in any other case the user wouldn’t be able to write or even to read the contents of the file. So, what if it is vulnerable? Then, the attacker can really easily supply the path traversal sequences. He will be able to complete such an action by using so-called dot-dot-slash characters. Once, he succeeds, he will break out the intended directory. Then, he has the access to write or read on any files which are located elsewhere on the filesystem. It is also important to remember that this vulnerability is very serious. What it does is that it literally enables the attackers to have the access to all of the sensitive data. Those can be files which contain some configuration data, the database’s records, different passwords, source code, program binaries or scripts etc.
File Path Traversal Impact
As I have already explained in the issue’s description part in this article, you have probably realized what dangerous damages can it make. Besides all that I have mentioned, the attacker can also step out from the root directory. Once he does that, he has the access to the whole filesystem, as described above. Do you want to keep your files registered and no one to see them? Well, it may be a problem once you get vulnerable to this issue. The attacker can make such powerful commands and totally execute a full compromise on your system. Hope not yours, but I also hope no ones.
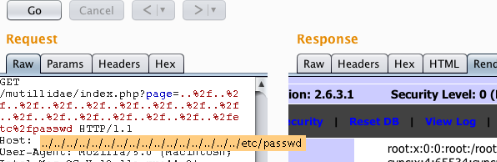
Example Of File Path Traversal
Let’s say that the app has the dynamic page. Here, the input is most of the times received from the browsers via GET or POST requests. Those are the two most common methods which are used. I will show you now how does it look like when it is done through the GET method!
GET http://test.webarticles.com/show.asp?view=oldarchive.html HTTP/1.1
Host: test.webarticles.com
What happens with this URL is that the browser here requests the dynamic page (show.asp) from a server. After that, the view parameter is also sent. It goes within the value of oldarchive.html. Later on, it needs to be rendered and sent back to the server. It will then be displayed to the user.
Recent Attacks Of File Path Traversal And Impact
I hope that you have understood that the code is the one that is most of the times vulnerable. That is how these attacks work. But, it is very important to remember a web server can also be open to these serious file path traversal attacks. Sometimes, the whole thing is actually incorporated into the web server’s software. It can also happen that it can appear inside some basic or sample script file which was left available on that server.
How To Fix File Path Traversal
The best way to fix it is to prevent it, like always! What should the app’s functionality look like? It must be designed in a way which would provide that the user-controllable data doesn’t even need to pass to the filesystems operations. How to achieve such an action? You must reference the known files through the index number. Don’t do it under a name, ever. Also, always use the app-generated filenames when it comes to saving those user-supplied file content. How to check if you are vulnerable? Simply, by using the Web Vulnerability Scanner! It will scan everything needed and then report it. What should you do then? fix it if vulnerable!
Enjoyed this lesson? We have so much information to share with you! Keep yourself safe in the cyber world!
