
What is Network Address Translation?
We have been talking a lot about the proxy servers which are also used in the Network Address Translation(NAT). We implement proxies to convert the private address to the public address.
The NAT allows us to use the IP address before the public address. The Network Address Translation enhances caching, allows the multiple computers share the public address, and masks the servers from being attacked by the malicious web addresses.
The NAT router helps to translate the unregistered (inside, local) IP address to a registered IP address. When you run a company, there are chances that some of the computers communicate inside the local addresses while on the other hand a few may connect to the outside network.
For the outside network communication, the packet goes to one of the NAT routers. It will then check for the entry of the destination address in the router table . If the entry matches the packet is allowed to pass through, but if the entry doesn’t match the packet is dropped. Now from the outside global address the information will transmit to the private network.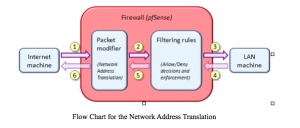
Virtual Private Network (VPN) Connectors
The number of internet users across the globe has increased drastically.Hence, with the help of Virtual Private Network Connectors we need to secure the remote connectivity to our private network for smooth work at home or the workplace.
A VPN Connector will ensure that your traffic moves within a tunnel,that is, called as the Virtual Private Network. It will save your network communication from the malicious users who can eavesdrop your data packet.
The VPN connector makes sure that the traffic that goes in is decrypted and that comes out is encrypted.
So we can can put in simple words that a VPN Connector
- It establishes or configures the tunnel for easy traffic movement
- It authenticates the users
- Assigns tunnel/IP address to the users
- Encrypts and Decrypts the data
- Ensures the delivery of data (end-to-end) point
By now, you know that a smooth network operation is a basic requisite for any organization to grow. Hence, we ought to have some Network Administration Principles to maintain the smooth operations. The traffic that enters the network should abide by these principles and the traffic that would be denied the access should also follow these rules.
Always know that if the router is not configured properly, all kind of traffic will enter the network. Without the rule-based management, the malicious internet users, can harm our working. Some rules should dictate the entry or the exit of the data packets. The Firewalls/ Antivirus/Routers/Proxies, etc. are some of the examples based on the Rule Based Security Management.
We should secure routers with passwords.The Secure Router Management prevents the malicious users to damage or alter the router table inside the router.
The Access Control Lists is generated inside the Firewalls.The systems have the list of the users who can have access to the network and those who will be denied access. In other words, it will define the capabilities of the systems that can have admission approval through the network.
It is a security measure for the routers, switches, and the firewalls.
Port Security
It deals with the logical and physical security. Under the Physical Port Security, the devices are locked down to have the physical access to the ports so that the malicious users do not have connectivity to the ports. Whereas under the Logical Port Security, the ports can be disabled within the system.
Another option to deal with the situation is to install the smart patch panel that would monitor the MAC address of the system which is connected to an empty port. To check for the port security, it is about checking the TCP and UDP ports. If a service is assigned to a port, then the port is active and the rest two ports are inactive.
