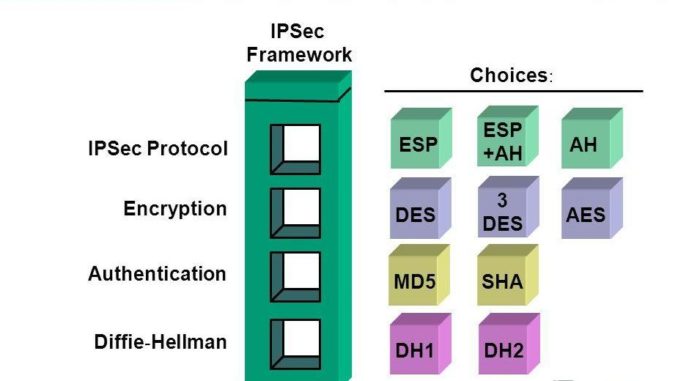
MD5
The MD 5 algorithm is used as a hash function that produces 128 bit hash value. It is widely used in the software world to ensure the delivery of the transferred file. The delivery is said to be intact with the MD 5.
However, the technique is said to be compromised as the person who created the file can create a second file with the same checksum, and so it cannot protect against any form of malicious tampering.
SHA
Secure Hash Algorithm is a cryptographic hash functions published by NIST.
AES
The Advanced Encryption Standard is the US government standard for the secure exchange of sensitive but classified data. It uses key lengths and block sizes of 128, 192 and 256 bits to achieve a high level of security. It is better than Data Encryption Standard (DES) Algorithm.
