What is DOM based cross site scripting?
Web developers are working hard round the clock to test websites for loopholes that can be exploited, and attackers are working hard to find vulnerabilities in the code to provide internet user with the most relevant cyber security tips. One such web application vulnerability is cross-site scripting also known as the XXS vulnerability.
Based on a vital concept in the web application security model in computer language, the same-origin policy permits the second web page to access data on the first if they have the same origin. Parameters used to determine the presence of same-origin are gauged by URI scheme, port number and hostname. What a cross-site scripting seeks to bypass controls by exploiting the presence of same-origin policy.
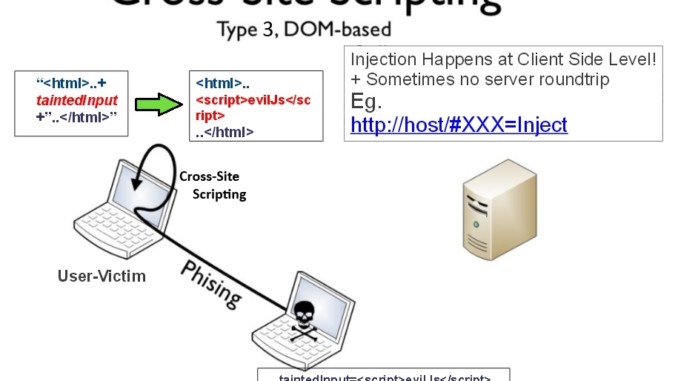
A Document Object Model based cross-site scripting is simply a vulnerability that appears in the DOM instead part of the HTML. It is vulnerability on the client side of the code due to DOM objects that are not fully controlled.
The impact of types of CSS vulnerabilities:
A well-known vulnerability users are warned of in both internet security tips and mobile phone security tips are one of the most common web application amongst developers is the DOM based CSS vulnerability.
An impact of the most basic type of web vulnerability – a reflected attack, causes the victim’s browser to successfully execute the injected script by using a harmless looking URL as bait. An attack usually delivered via email contains a URL to a trusted site whilst containing the CSS vector, therefore, causing successful execution on the site vulnerable to the vector. Comparatively, a persistent or stored vulnerability is much more damaging with devastating outcomes. This occurs when the data modified by the attacker and saved on the pages for other users to see in their course of browsing without proper HTML sifting.
However, DOM based CSS modifies the environment in the victim’s browser using the original script on the client side. So basically, modifications made to the client side browser enable the HTTP response to run normally, but due to the malicious changes made to the server, it executes differently.
Examples and recent attacks
An example of how a DOM based CSS vulnerability is when the URL is sent the server responds with the code that creates a DOM object for the page, because of the unexpected response the browser renders the code and executes the attacker’s script.
An XSS attack applied a different DOM based XSS variants to PDF documents. When it was rendered by the Acrobat plugin, this in return may result in the fragment being executed as Javascript. Due to all the attacker needed to exploit an existing flaw was find a PDF link on the site for the XSS condition to be met because in context to DOM the Javascript is already executed in context to DOM.
Another attack aimed to target people who click malware-infected URLs whilst having their google accounts logged in.
How to fix/avoid a DOM based CSS attack?
In order to fix and counter DOM based CSS attacks, it is important to decide whether the idea is to prevent and test vulnerabilities and loopholes for the purposes of prevention from a developers perspective or prevention and fixes from clients. Extensive research into DOM based CSS attacks has led to the development vital tools that serve and add to cyber security tips for web users. Tools testing for vulnerabilities are:
The DOMinator tool is a commercial tool with modified javascript that assists in identifying and verifying DOM CSS vulnerabilities.
DOM snitch enables testers and developers identify unsafe practices found in google from the client side.
For web developers seeking to stop XXS attacks, it is important to not to use user-provided data in an unfiltered way. It is also essential to use content security policy and other secure frameworks to encrypt flow of data at all times. Constant rigorous testing for vulnerabilities in plugins and built-in applications is vital to ensure the continuance of a safe client – consumer server relationship.
Conclusion
In order to maintain the privacy of personal information, it is of utmost importance to have the internet, mobile phone and social security tips on your fingertips. The internet is swarmed with people ready to take advantage of vulnerabilities in either a web developers code or a naive credit card udders pin; a DOM based CCS attack also called DOM based XXS attack, seeks to take control of the server from the client’s side, not only putting the entire existing customer database at risk but also every user that clicks on such malware ridden URLs.
