The following steps will be taken to show buffer overflow –
- PREP Kali Linux
- Create envexec.sh and vuln.c files and make envexec.sh Executable – Open the command prompt and do ‘ls’. We will use two files i.e. envexec.sh and vuln.c. If we look at the contents of envexec.sh we can see that it has a script which is cleaning up the bash environment and making an executable so that we can debug our vulnerable C program and it does this by running the GDP which is a debugger for the GCC compiler on kali Linux.
Vuln.c is a very basic C program with one function called main which returns zero. It has declared a character buffer of 500 and we’re going to string copy whatever forced into the main function and into the buffer. These characters should be less than or equal to 500. If we put anything over 500 we will get a buffer overflow.
- Compile – To compile the file, the command is –
gcc -z execstack -fno –stack protector –mpreferred-stack-boundary=2 –g vuln.c –o vuln
- Clean Bash Environment – To do this, run the following command –
./envexec.sh –d vuln
- Show the code – If we run this command the debugger is opened. Gdb has few commands through which we can look at the assembly code. main command shows exactly what the application is doing in assembly code.
- Run the program – We run the program by typing ‘run Hello’ where hello is a 5 character parameter passed to the program. The program executes successfully.
- Run the program with an overflow – To do this we will give the following command –
run $(python -c ‘print “\x41” “508”)
In this program we have given characters more than 508 so when we run this command the program will give an error.
- Look at the registers – Use the following command –
info registers
EBP as we can see it’s x414141 and ERP or instruction pointer which is the one we’re trying to overwrite is also x414141.
- Look at the memory addresses – To do this use command –
x/200x (esp – 550)
This command means show me the memory from ESP back 550. On running the command we can see the buffer has x414141.
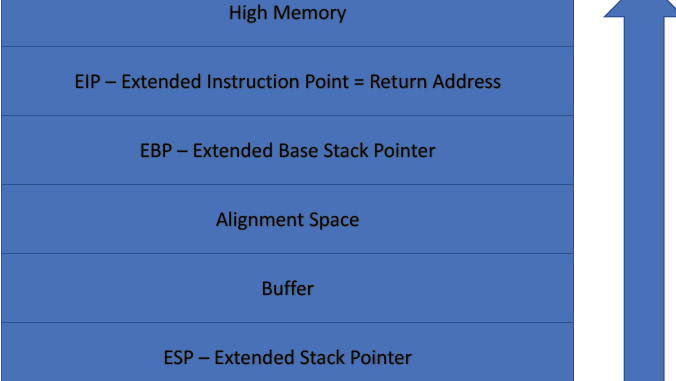
- Take control of the EBP (Extended Base Pointer) – When we want to run a buffer overflow we want to know exactly which characters are being written by the EBP. The script for this is –

Figure1. Script to take control of EBP
We are running a python script. We will print X90 which is the null pointer 426 times. Then then we will fill the buffer with code which is basically a shell command and then we will add \x51515151 at the end of that because this is actually what we want our EBP pick to be. We want to write over to our ERT and EBP with a memory address so that we can actually tell our CPU to go back and actually execute this code. It will just print it up but when we do the buffer overflow we want this exact address here to be a memory address so that we can trick the CPU into going back into the buffer and executing the code.
On running the code, we get a segmentation fault.
- Look at the registers – If we look at the registers we see that ERP is 515151 and EBP is 515151 and that’s exactly what we’re looking for.
- Look at the memory addresses – We can see the data we have entered. We want to change these 51s to one of these memory addresses so that when the program hits the ERP entries, it will be moved back into this memory address that will hit a null pointer and a null pointer will then paused until it hits a a piece of code that it can execute or a piece of memory that we can understand. This is called a NOP sled.
- Run the exploit with a ‘NOP’ sled – The command is –

Figure2. NOP sled exploit
Through this we will put our coding in the overflown buffer. On running the command Kali prompt will come where we can run our commands.
Ethical Hacking Tutorial – Buffer Overflow Lab Session Video:
