For this session,we will use a tool called ‘Security Onion’ which you can download from the internet. It has a whole host of reporting tools built into it so is quick to setup and run.
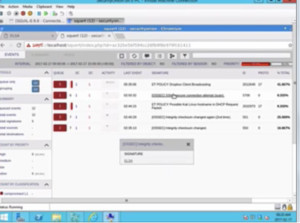
Figure1. Security Onion
Here we can see that few alerts are already there, as it was running for some time. There is an integrity checksum exchange, on clicking on which we can see the signature. There is a Kali Linux hostname, an SSH connection attempt, etc. We have another tool called ‘ELSA’.
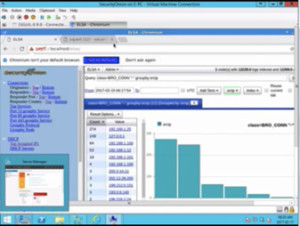
Figure2. ELSA
It shows the top originator and top responders by IP address and one can actually see what is happening. There is another tool called ‘Squil’. It is not a web based tool, but an application tool and gives alerts as and when they happen. For e.g. in this if we look at the SSH insecure and click on display detail we can see where the identification string came from so that I can track it further.
There is another tool called ‘pfsense’ which is a free file wall.
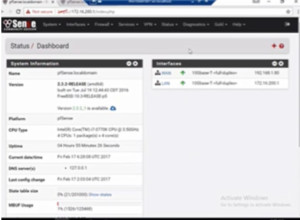
Figure3. pfsense
We will use the logging capability of the firewall to see IP address spoofing. If we go into System logs->Firewalls we can see some traffic floating around.
Now we will open Kali and check its I address. It is 192.168.1.102. We will run a simple nmap scan on this firewall which is 192.168.1.80. After the scan is finished, we can see in the dynamic view of pfsense that 198.168.1.102 is scanning many ports. Now we want don’t want to spoof the real IP address rather we will spoof another IP address so that the firewall administrator doesn’t come looking for us but rather go to look for some other poor victim. The command is –
nmap -T4 –A -e eth0 -S 192.168.1.199 192.168.1.80
Now if we see at the firewall logs we can see that it is reporting the source as 192.168.1.199. So the spoofing worked perfectly for the nmap scan and we can hide the true IP address just by using the –S, -e scripting options in nmap.
Now we will look at ‘tor’ and ‘proxychains’. We will reach the traffic through the tor network. This works well for applications on the internet and probably not work at all for this internal firewall. First run ‘tor’. Open another window. Now we will scan the firewalls using proxy chains. The command is –
proxychains nmap -tf -PN -n 192.168.1.80
We can see that it is going through the local host, port 9050 which is the tor port and eventually via the tor network and comes back.
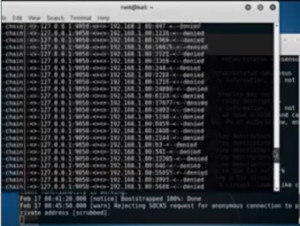
Figure4. proxychains output
It is showing a lot more ports than a standard nmap scan because it tells exactly what it is doing. One interesting thing is that if we actually run this scan and look at your firewall logs by running it through proxy chains it don’t show up in pfsense logs. So proxychains is a good way to hide and evade firewall logs in the real world.
Ethical Hacking Tutorial – Intrusion Detection Systems, FireWalls, HoneyPots Lab Session Video:
